A time of reflection: Five tips for Financial Services in 2019
OpenText Information Management
JANUARY 10, 2019
The New Year is upon us, and with it come new challenges and opportunities for the Financial Services industry.

OpenText Information Management
JANUARY 10, 2019
The New Year is upon us, and with it come new challenges and opportunities for the Financial Services industry.

AIIM
FEBRUARY 22, 2018
Nowhere is this truer than in the financial services sector. In a recent AIIM survey, 85% of finance and insurance executives said that digital preservation was “important” or “very important” to their organizations – even higher than the 77% reported in other industries.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Data Matters
APRIL 20, 2021
The Cybersecurity Guidance is set forth in three parts: Tips for Hiring a Service Provider , directed toward plan sponsors and fiduciaries. Online Security Tips for plan participants and beneficiaries. Plan sponsors and fiduciaries should carefully review the full list of Tips for Hiring a Service Provider.
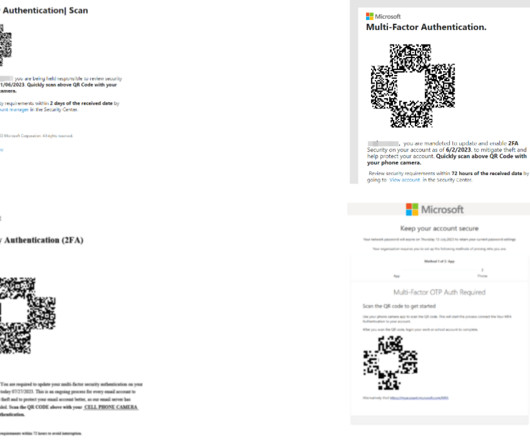
Security Affairs
AUGUST 16, 2023
Other top 4 targeted industries include Manufacturing, Insurance, Technology, and Financial Services seeing 15%, 9%, 7%, and 6% of the campaign traffic respectively.” Experts warn that the Energy sector was a major focus of this campaign, followed by manufacturing, and insurance. ” continues the report.

The Last Watchdog
JANUARY 30, 2019
Turn the corner into 2019 and we find Citigroup, CapitalOne, Wells Fargo and HSBC Life Insurance among a host of firms hitting the crisis button after their customers’ records turned up on a database of some 24 million financial and banking documents found parked on an Internet-accessible server — without so much as password protection.

KnowBe4
MARCH 28, 2023
Strategies include: Developing a comprehensive, defense-in-depth plan Technical controls all organizations should consider Gotchas to watch out for with cybersecurity insurance Benefits of implementing new-school security awareness training Best practices for creating and implementing security policies Get the E-Book now!

Adam Levin
SEPTEMBER 5, 2019
Your phone provider will have tips on the best practices to avoid SIM-card attacks, and common sense can be your guide regarding any unexpected phone calls, and practice the Three Ms: Minimize your exposure. It is believed this was the method used to recently hack Jack Dempsey’s Twitter account. . What You Can Do.
Let's personalize your content