China-linked threat actors are targeting the government of Ukraine
Security Affairs
MARCH 18, 2022
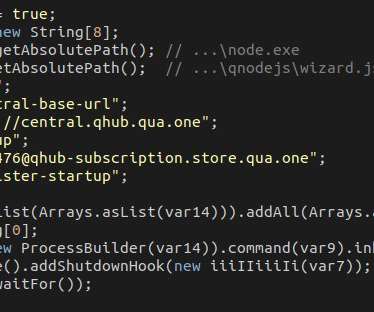
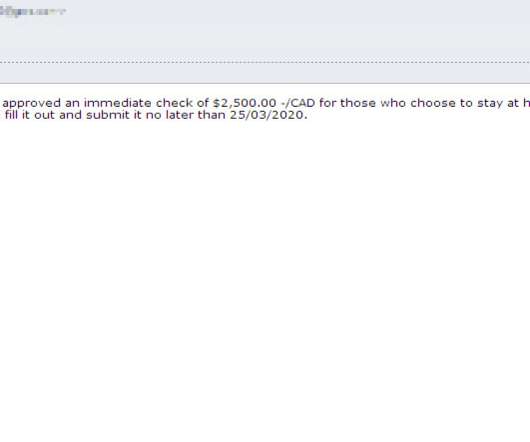
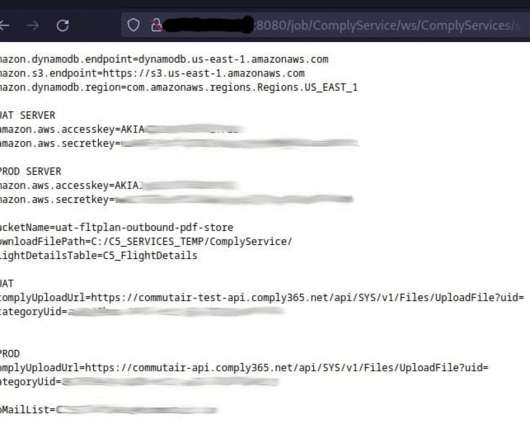
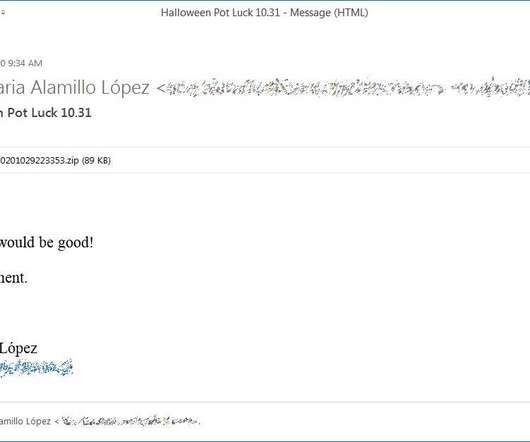
Google’s TAG team revealed that China-linked APT groups are targeting Ukraine’s government for intelligence purposes. Google TAG team notified Ukrainian government organizations that were targeted by Chinese intelligence. government. government. China is working hard here too. Pierluigi Paganini.


































Let's personalize your content