What is the vulnerability management process?
IBM Big Data Hub
SEPTEMBER 6, 2023
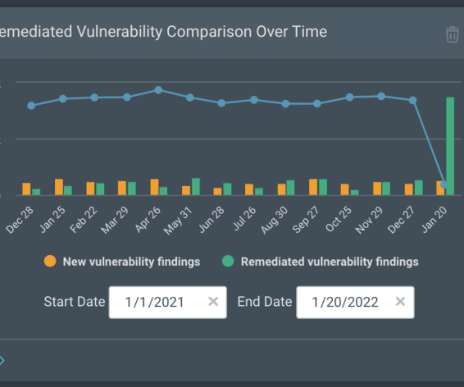
Modern enterprise networks are vast systems of remote and on-premises endpoints, locally installed software, cloud apps , and third-party services. Every one of these assets plays a vital role in business operations—and any of them could contain vulnerabilities that threat actors can use to sow chaos. Coding errors—e.g.,












































Let's personalize your content