Be Very Sparing in Allowing Site Notifications
Krebs on Security
NOVEMBER 17, 2020
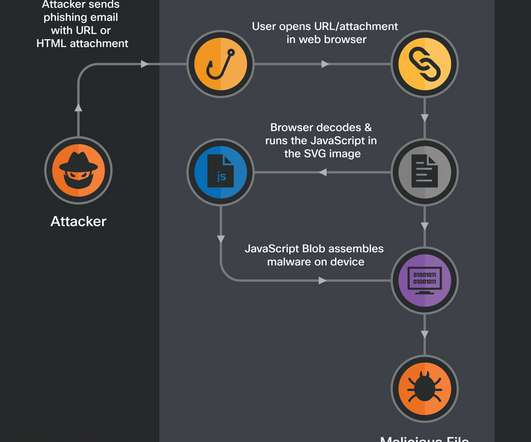
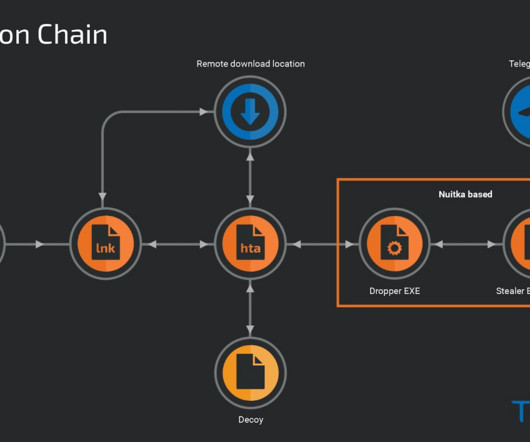
An increasing number of websites are asking visitors to approve “notifications,” browser modifications that periodically display messages on the user’s mobile or desktop device. For example, on Microsoft Windows systems they typically show up in the bottom right corner of the screen — just above the system clock.








































Let's personalize your content