Data Security: Think Beyond the Endpoint
Dark Reading
MAY 20, 2019
A strong data protection strategy is essential as data moves across endpoints and in the cloud.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 endpoint-security data-security-think-beyond-the-endpoint
endpoint-security data-security-think-beyond-the-endpoint 
Dark Reading
MAY 20, 2019
A strong data protection strategy is essential as data moves across endpoints and in the cloud.

The Last Watchdog
JULY 1, 2022
This raises the concerns of corporate data security in remote working that still stand as a key challenge that organizations are trying to navigate, workforce productivity being the second. Managing endpoints securely . Related: Deploying human sensors. Fragmentation dilemma .
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
FEBRUARY 28, 2022
However, APIs have gained traction so rapidly and deeply that not nearly enough attention has been paid to the associated security shortcomings. Many organizations, SMBs and enterprises alike, do not understand the scope and scale of their deployments of APIs, much less how to go about effectively securing their APIs. API complexity.

The Last Watchdog
FEBRUARY 7, 2023
Using legitimate services and compromised corporate email addresses became a norm and is likely to continue in 2023 and beyond. Another report by Vade completed last year found that 87 percent of respondents agreed their organization could take the threat from email security more seriously. This is a harmful misconception.

The Last Watchdog
NOVEMBER 14, 2022
Matter certified smart home devices will respond reliably and securely to commands from Amazon Alexa , Google Assistant , Apple HomeKit or Samsung SmartThings. Think of it: consumers will be able to control any Matter appliance with any iOS or Android device. This time we drilled down on the security pedigree of Matter 1.0.
eSecurity Planet
APRIL 5, 2022
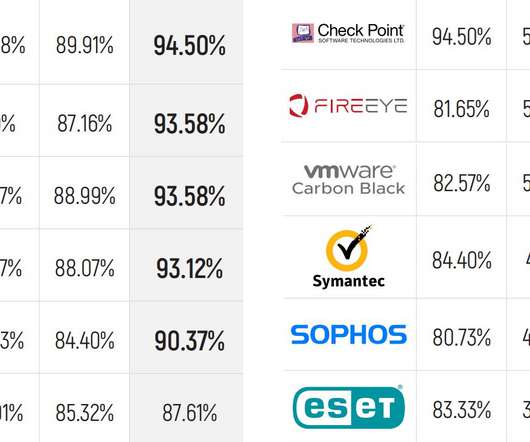
MITRE Engenuity has released the latest round of its ATT&CK endpoint security evaluations, and the results show some familiar names leading the pack with the most detections. MITRE doesn’t score results or try to say who “won,” and instead just provides the raw data. MITRE Methodology and Adversaries.

eSecurity Planet
DECEMBER 13, 2021
Germany-based G Data CyberDefense released software designed to trick the STOP ransomware variant into believing that a targeted system has already been compromised and keeping it from encrypting files after the device has been infected. So I guess STOP thinks those files were successfully encrypted and hence renames them.”.

eSecurity Planet
AUGUST 22, 2023
Remote access security is critical for protecting increasingly distributed work environments, ensuring that only authorized users can access your valuable information regardless of their location. The technologies for secure remote access can range from VPNs and multi-factor authentication to more advanced access and zero trust controls.

The Last Watchdog
MAY 11, 2021
By patiently slipping past the best cybersecurity systems money can buy and evading detection for 16 months, the perpetrators of the SolarWinds hack reminded us just how much heavy lifting still needs to get done to make digital commerce as secure as it needs to be. Related: DHS launches 60-day cybersecurity sprints. Advanced cloaking.

Lenny Zeltser
AUGUST 23, 2023
Start by critically reviewing how you’ll spend the security funds; this involves broadening your perspective beyond security. This way of thinking about cybersecurity brings CISOs closer to the world of CIOs. To do this, you may need to work with the finance team to itemize the expenses allocated to security at your firm.

ForAllSecure
FEBRUARY 23, 2023
All of these APIs have one thing in common: they need to be secure. Unfortunately, many devs and ops engineers don't view API security as a priority - and that's a mistake. In this blog post, we'll explore why API security is so important, and how you can make sure you're doing it right. Or something else entirely.

The Last Watchdog
FEBRUARY 12, 2019
Assuring the privacy and security of sensitive data, and then actually monetizing that data, — ethically and efficiently — has turned out to be the defining challenge of digital transformation. Today a very interesting effort to address this complex dilemma is arising from the ferment, out of the UK.

IT Governance
FEBRUARY 27, 2020
Technological defences and staff training are two of the most frequently touted measures for preventing data breaches, but their effectiveness is dependent on the way organisations implement them. That means creating a detailed cyber security policy. What is a cyber security policy? What a cyber security policy should include.

eSecurity Planet
JULY 30, 2021
Endpoint security is a cornerstone of IT security. To help you navigate this growing marketplace, our team has researched and analyzed this list of top endpoint detection and response (EDR) vendors. EDR, EPP and endpoint security steps. Jump ahead to: Other market leaders. Feature comparison. Methodology.

ForAllSecure
JUNE 16, 2021
APIs are vital in our mobile digital world, but the consequences of API security flaws have yet to be seen. What's on your mobile than our external API's and in the past few years there's been an explosion of external API data. Lascelles: Yeah, and this, this is a huge lesson in API security right hackers are also users.

ForAllSecure
JUNE 16, 2021
APIs are vital in our mobile digital world, but the consequences of API security flaws have yet to be seen. What's on your mobile than our external API's and in the past few years there's been an explosion of external API data. Lascelles: Yeah, and this, this is a huge lesson in API security right hackers are also users.

The Falcon's View
AUGUST 6, 2018
There's no shortage of guidance available today about how to structure, build, and run a security program. At end of day, the goal of your security program should be to chart a path to an optimal set of capabilities. That said, what exactly constitutes "basic security hygiene"? But, I digress. The Basics. Applications. -
Adam Shostack
JULY 1, 2021
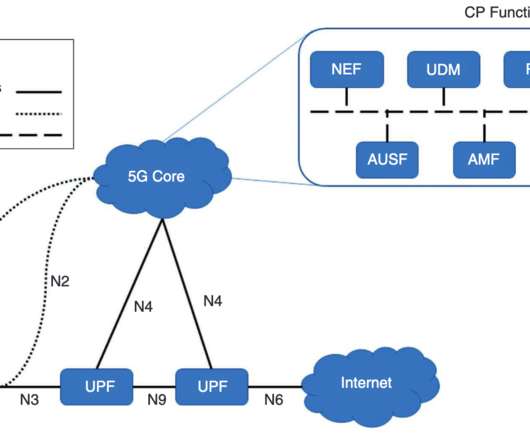
I think the report from a Threat Model Working Panel of the Enduring Security Framework of CIPAC, but then there’s language like “identified by the ESF and 5G TM working panel… (emphasis added)” which implies its separate. The data gathered by 5G? What are we working on? Is it the networks?

eSecurity Planet
DECEMBER 19, 2023
Without guidelines, organizations risk unfettered use of AI, risks of data leaks, and no recourse for unethical AI use within the organization. For more on governance and policies, check out our article on IT security policies , including their importance and benefits, plus tips to create or improve your own policy.

The Last Watchdog
OCTOBER 17, 2023
Cisco’s recent move to acquire SIEM stalwart Splunk for a cool $28 billion aligns with the rising urgency among companies in all sectors to better protect data — even as cyber threats intensify and disruptive advancements in AI add a wild card to this challenge. Related: Will Cisco flub Splunk? Last Watchdog engaged Gurucul CEO Saryu K.

eSecurity Planet
DECEMBER 9, 2021
We make IT, security, or any business decision by weighing the risks and the rewards. Or as is often the case with security, what costs can we skip and still escape big penalties later? Unfortunately for those of us indulging in wishful thinking, the likelihood and costs of data breaches continue to increase.

eSecurity Planet
APRIL 11, 2022
Security vendors and startups use deception techniques to confuse and befuddle attackers. By masking high-value assets in a sea of fake attack surfaces, attackers are disoriented and attack a fake asset, in the process alerting security teams to their presence. But it can work the other way. What is Deception Technology?

ForAllSecure
AUGUST 30, 2022
The governments of the world wanted the quick and agile minds of children who could think three dimensional -- and without all that moralizing about killing, you know, space aliens. I’m Robert Vamosi and in this episode I’m talking about cyber ranges-- simulations that can both teach and improve the security of your networks.

Brandeis Records Manager
JULY 28, 2016
After reflection on my academia colleague’s survey questions, I came to the conclusion that, while RIM/IG is a curious fit within the academic library and archives culture, I couldn’t think of another place in my organization where my program would perfectly align. Interesting stuff, but beyond my job function.

eSecurity Planet
MARCH 22, 2023
Networks connect devices to each other so that users can access assets such as applications, data, or even other networks such as the internet. Network security protects and monitors the links and the communications within the network using a combination of hardware, software, and enforced policies.

The Last Watchdog
JUNE 6, 2022
Many are working with siloed security products from another era that serve as mere speed bumps. Meanwhile, security teams are stretched thin and on a fast track to burn out. Meanwhile, security teams are stretched thin and on a fast track to burn out. Beyond silos. Pity the poor CISO at any enterprise you care to name.

The Last Watchdog
AUGUST 29, 2018
If digital transformation, or DX , is to reach its full potential, there must be a security breakthrough that goes beyond legacy defenses to address the myriad new ways threat actors can insinuate themselves into complex digital systems. A cottage industry of tech security vendors is fully behind NTA. Think candy store. “In

eDiscovery Daily
JANUARY 30, 2018
be interviewing several industry thought leaders to see what they think are the significant trends for 2017 and, which of those are evident at LTNY. Will we see lawyers subpoena the connected car for its sensor data? While at the show, we will (for the eighth year in a row!) While at the show, we will (for the eighth year in a row!)

eSecurity Planet
OCTOBER 1, 2022
With two high-profile breaches this year, Okta, a leader in identity and access management (IAM) , made the kind of headlines that security vendors would rather avoid. During that time, the client accessed Okta’s customer support panel, data for two of Okta’s 15,000 customers, and local applications such as Slack and Jira.
eSecurity Planet
OCTOBER 5, 2021
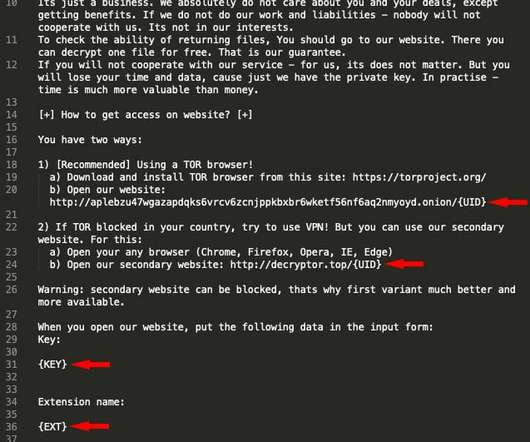
Install layered security. Test both security and policies for effectiveness. Ransomware Security. When installing layered security we need to focus on the most likely target and the most likely attack paths. We should encrypt data at rest. So easy to say, so difficult to do correctly. Ransomware Response.

KnowBe4
JULY 5, 2023
But I don't think an attack of such magnitude as the one identified by security researchers at Internet security monitoring vendor Bolster. This latest impersonation campaign makes the case for ensuring users are vigilant when interacting with the web – something accomplished through continual Security Awareness Training.

Thales Cloud Protection & Licensing
JULY 6, 2022
Think Zero Trust Applies Only to Federal Agencies? Think Again! Beyond the Public Sector. Danna Bethlehem, Director of Product Marketing Identity & Access Management (IAM) at Thales, said she doesn’t think that federal agencies will be the only ones to use the E.O Thu, 07/07/2022 - 05:42. around implementing zero trust.

Thales Cloud Protection & Licensing
APRIL 21, 2021
But behind the scenes, this emergence of often untrusted devices (BYOD) and an increased adoption of unsanctioned applications (a trend called “Shadow IT”) has led to security nightmares for IT departments. The path to a Zero Trust posture is not linear, and the tall claims by security vendors often cloud the decision-making.

ForAllSecure
APRIL 19, 2023
It’s time to evolve beyond the UNIX operating system. Maybe I’m thinking about Dan because of that anniversary. OSes today are basically ineffective database managers, so why not build an OS that’s a database manager? You can learn more at dbos-project.github.io. Dan found a flaw that could have crippled the internet.

ForAllSecure
JUNE 21, 2022
Kyle Hanslovan CEO of Huntress Labs joins The Hacker Mind to discuss recent LoL attacks, specifically the Microsoft Follina attack and the Kaseya ransomware attack, and how important it is for small and medium sized businesses to start using enterprise grade security, given the evolving nature of these attacks. Think of it as a Trojan horse.

Troy Hunt
FEBRUARY 21, 2018
This was a list of 320 million passwords from a range of different data breaches which organisations could use to better protect their own systems. Back at the V1 launch, I explained how the original data set was comprised of sources such as the Anti Public and Exploit.in

The Last Watchdog
DECEMBER 27, 2021
Related: The dire need to security-proof APIs. On the privacy front, California beefed up its consumer data privacy regulations even as Facebook and Apple publicly feuded over how each of these tech giants abuse of consumer privacy and loosey handle sensitive data. The answer for many is SaaS Security Posture Management ( SSPM.),

KnowBe4
MAY 31, 2023
That's right – the financial services industry, at least according to cybersecurity vendor Armorblox's 2023 Email Security Threat Report. Blog post with links: [link] [Live Demo] Ridiculously Easy Security Awareness Training and Phishing Old-school awareness training does not hack it anymore. When you want tires, where do you go?

Reltio
JULY 23, 2019
Steve Whiting is the COO of Agile Solutions (GB) Ltd, a specialist data management and analytics consultancy that focuses on tangible business benefits. He believes in an agile approach to data-driven solutions and co-founded Agile Solutions in 2014 to deliver that vision.

ForAllSecure
MARCH 22, 2023
We’ve seen drug marketplaces and extremists use the Dark Web. Will generative AI tools like ChatGPT make things crazier by lowering the barrier to entry? She discusses what is and what is not likely to happen next. VAMOSI: We hear a lot about the Dark Web. We hear a lot of hyperbole. George, good morning to you. Those are the headlines.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content