Attacks Escalating Against Linux-Based IoT Devices
eSecurity Planet
JANUARY 20, 2022
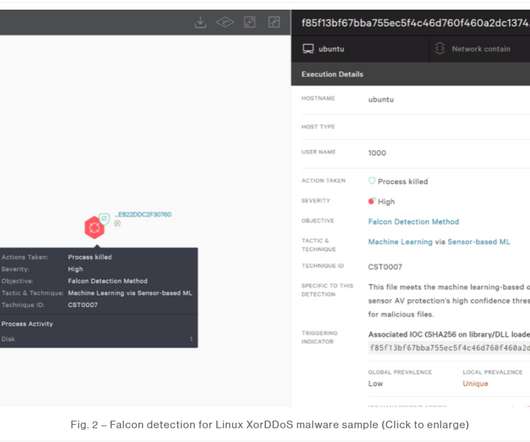
Incidents of malware targeting Linux-based Internet of Things (IoT) devices jumped by more than a third in 2021, with three malware families the primary drivers behind the increase. However, with more than 30 billion IoT devices expected to be connected to the internet by 2026, attacks against them can have wide-ranging impacts.















Let's personalize your content