EvilProxy Phishing-As-A-Service With MFA Bypass Emerged In Dark Web
Security Affairs
SEPTEMBER 5, 2022
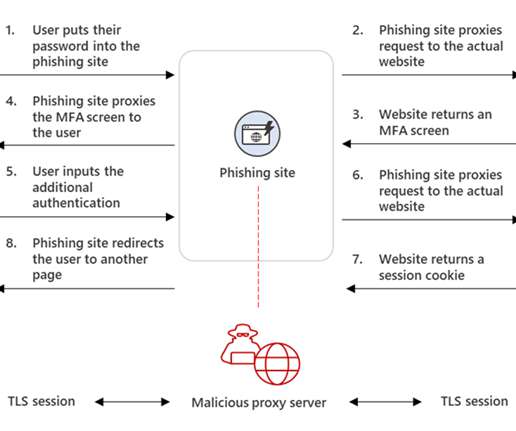
Resecurity researchers discovered a new Phishing-as-a-Service (PhaaS) called EvilProxy advertised on the Dark Web. Resecurity has recently identified a new Phishing-as-a-Service (PhaaS) called EvilProxy advertised in the Dark Web. The service is represented on all major underground communities including XSS , Exploit and Breached.


















Let's personalize your content