Kroll Employee SIM-Swapped for Crypto Investor Data
Krebs on Security
AUGUST 25, 2023
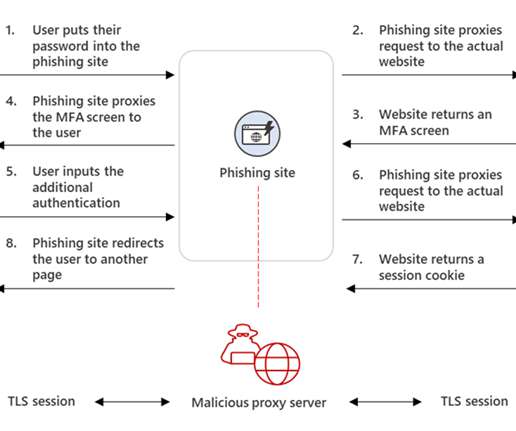
Security consulting giant Kroll disclosed today that a SIM-swapping attack against one of its employees led to the theft of user information for multiple cryptocurrency platforms that are relying on Kroll services in their ongoing bankruptcy proceedings. ” T-Mobile has not yet responded to requests for comment. .”








































Let's personalize your content