Weekly Update 384
Troy Hunt
JANUARY 27, 2024
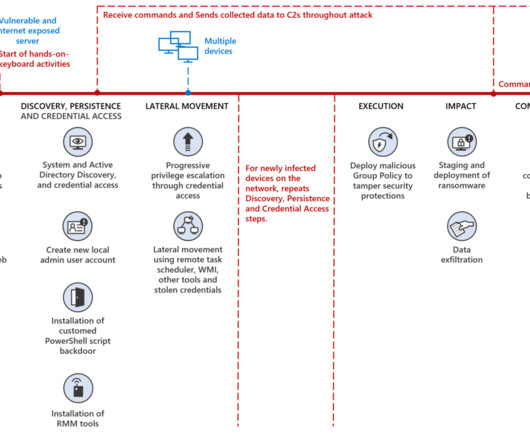
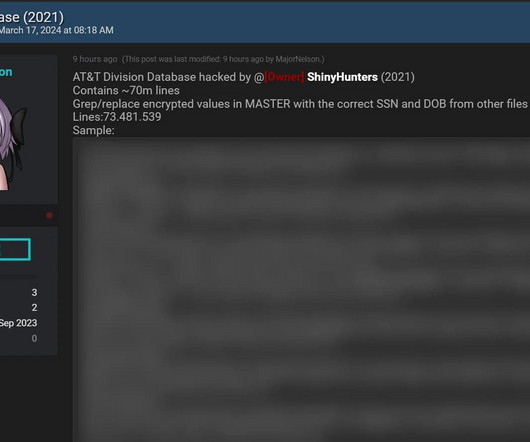
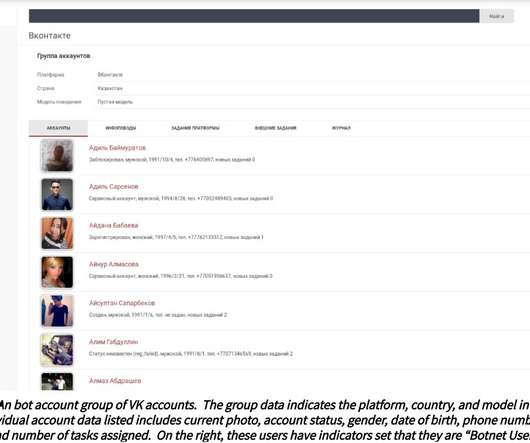
To add some more perspective, I've just posted a poll immediately before publishing this blog post, let's see what the masses have to say: Scraping: should we be concerned if an individual's personal data is scraped, aggregated en mass and redistributed if that same data is already publicly accessible on the service anyway?











































Let's personalize your content