Chinese APT Group Uses New Tradecraft to Live Off the Land
Data Breach Today
JUNE 26, 2023
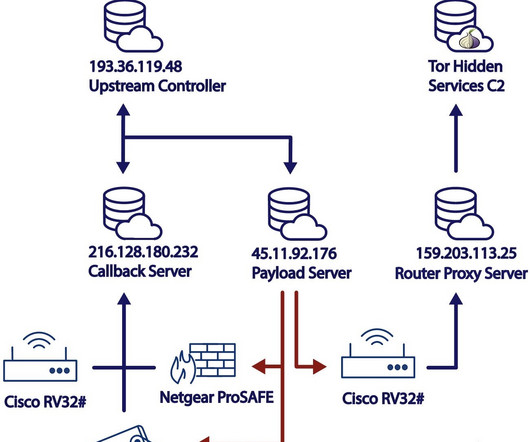
Targeted organizations include those in the communications, manufacturing, utility, transportation, construction, maritime, government, IT and education sectors.




































Let's personalize your content