GUEST ESSAY: Advanced tools are ready to help SMBs defend Microsoft 365, Google Workspace
The Last Watchdog
FEBRUARY 7, 2023
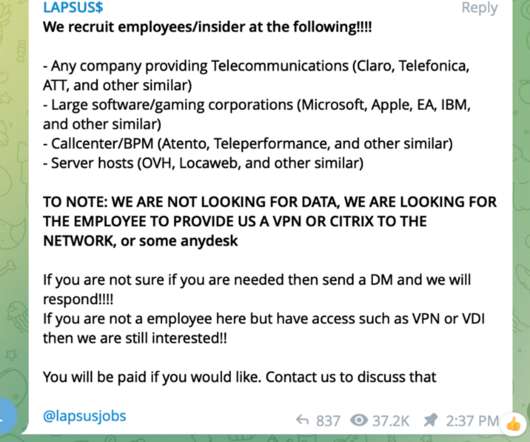
Throughout 2022, we saw hackers become far more sophisticated with their email-based cyber attacks. Related: Deploying human sensors Additionally, with tools like ChatGPT, almost anyone can create new malware and become a threat actor. This is a harmful misconception.
















































Let's personalize your content