Author Q&A: Here’s why the good guys must continually test the limitations of ‘EDR’
The Last Watchdog
OCTOBER 30, 2023
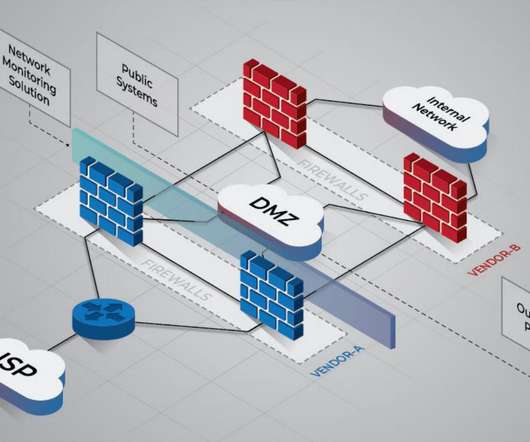
Windows is a very complex operating system and there are a ton of native capabilities that attackers can leverage. LW: Your book is targeted to precious commodity: experienced cybersecurity professionals. Perimeter defense has also been around for ages, but now the nature of the perimeter is changing.












































Let's personalize your content