Attackers use website contact forms to spread BazarLoader malware
Security Affairs
MARCH 12, 2022
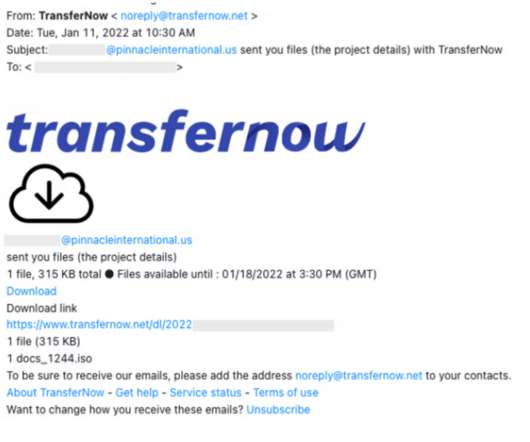
Researchers from cybersecurity firm Abnormal Security observed threat actors spreading the BazarLoader/BazarBackdoor malware via website contact forms. The security firms rapidly updated their solution to detect these campaigns forcing the threat actors behind the malware to use new techniques to deliver the malware.


















Let's personalize your content