GUEST ESSAY: Making the case for leveraging automation to eradicate cybersecurity burnout
The Last Watchdog
MAY 2, 2023
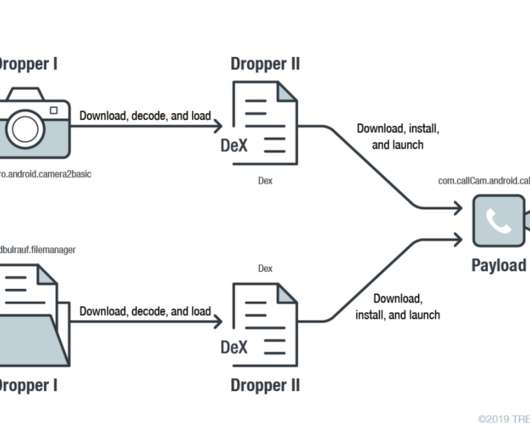
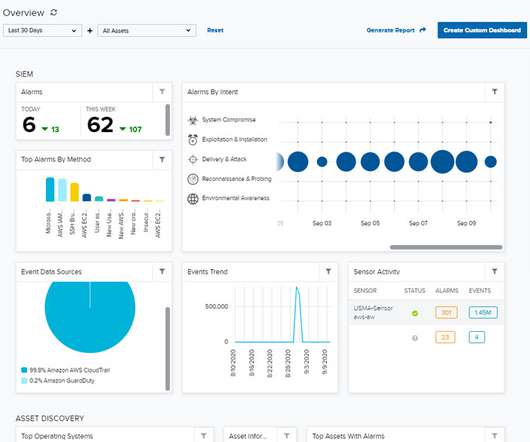
Related: Training employees to mitigate phishing It pressures working analysts to perform 24 hours’ worth of work in an 8-hour day. Experts must monitor firewalls, test business continuity plans and identify vulnerabilities with seemingly little payoff. Install software and hardware updates to minimize vulnerabilities.




















Let's personalize your content