MY TAKE: Poorly protected local government networks cast shadow on midterm elections
The Last Watchdog
SEPTEMBER 14, 2018
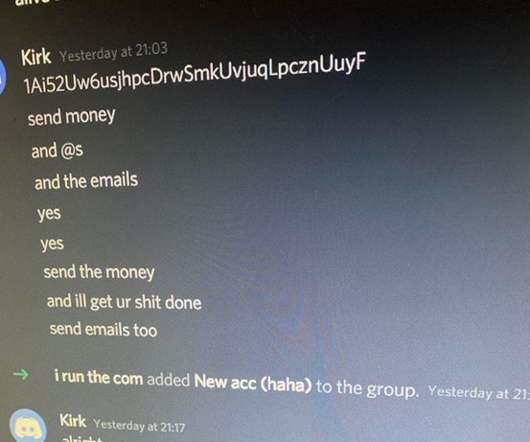
EventTracker has a bird’s eye view; its unified security information and event management (SIEM) platform includes – behavior analytics, threat detection and response, honeynet deception, intrusion detection and vulnerability assessment – all of which are coupled with their SOC for a co-managed solution. Election threat.















Let's personalize your content