New SPIKEDWINE APT group is targeting officials in Europe
Security Affairs
FEBRUARY 29, 2024
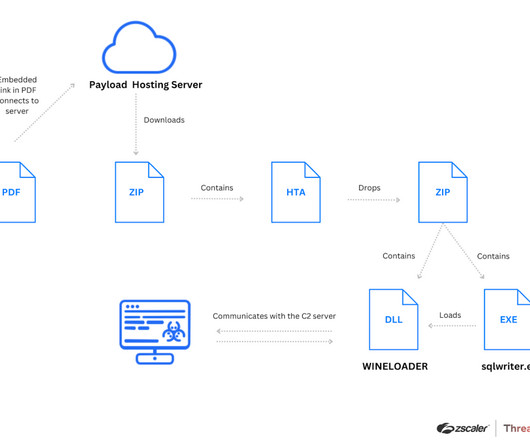
The evidence collected by Zscaler suggests that this campaign has been active since at least July 6, 2023. The threat actor used compromised websites for hosting intermediate payloads or to act as C2 servers. The researchers pointed out that WINELOADER is not injected into the DLLs that contain exported functions used by the malware.



































Let's personalize your content