Want to Improve Cloud Security? It Starts with Logging
Dark Reading
APRIL 3, 2020
Remedying the "garbage in, garbage out" problem requires an understanding of what is causing the problem in the first place.
This site uses cookies to improve your experience. By viewing our content, you are accepting the use of cookies. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country we will assume you are from the United States. View our privacy policy and terms of use.

 cloud-security want-to-improve-cloud-security-it-starts-with-logging
cloud-security want-to-improve-cloud-security-it-starts-with-logging 
Dark Reading
APRIL 3, 2020
Remedying the "garbage in, garbage out" problem requires an understanding of what is causing the problem in the first place.

The Last Watchdog
MAY 24, 2022
Excising passwords as the security linchpin to digital services is long, long overdue. Security + efficiency. Password abuse at scale arose shortly after the decision got made in the 1990s to make shared secrets the basis for securing digital connections. Threat actors now routinely bypass these second-layer security gates.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Krebs on Security
AUGUST 22, 2023
Security experts say this same tourist dynamic is a dead giveaway in virtually all computer intrusions that lead to devastating attacks like data theft and ransomware, and that more organizations should set simple virtual tripwires that sound the alarm when authorized users and devices are spotted exhibiting this behavior.
Security Affairs
NOVEMBER 21, 2022
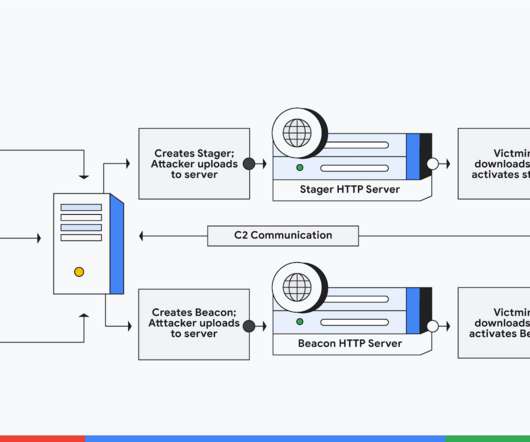
Researchers at Google Cloud identified 34 different hacked release versions of the Cobalt Strike tool in the wild. The Beacon includes a wealth of functionality for the attacker, including, but not limited to command execution, key logging, file transfer, SOCKS proxying, privilege escalation, mimikatz, port scanning and lateral movement. .

IBM Big Data Hub
DECEMBER 19, 2023
As enterprises embrace cloud native and everything as code, the journey from code to production has become a critical aspect of delivering value to customers. Stage 1: Development automation Infrastructure automation (IaC) and pipeline automation are self-contained within the development team, which makes automation a great place to start.

Thales Cloud Protection & Licensing
SEPTEMBER 14, 2023
Thales & Prime Factors’ 30 Year Collaboration Continues to Deliver Simplicity, Flexibility, and Security for Payment Applications madhav Thu, 09/14/2023 - 10:25 Thales recently announced the launch of the payShield Cloud HSM service , making it easier and more flexible for payment HSMs to migrate to the cloud.

IBM Big Data Hub
SEPTEMBER 6, 2023
Modern enterprise networks are vast systems of remote and on-premises endpoints, locally installed software, cloud apps , and third-party services. The vulnerability management process is a continuous process for discovering, prioritizing, and resolving security vulnerabilities across an organization’s IT infrastructure.

The Last Watchdog
MAY 3, 2021
I had the chance to learn more about ABE from Brent Waters, a distinguished scientist in the Cryptography & Information Security (CIS) Lab at NTT Research. Top mathematicians have been hammering away at improving encryption since before World War II. Refer: The vital role of basic research. Customized keys.

Imperial Violet
OCTOBER 20, 2021
With Chrome 94, if you have an Android phone with Chrome on it, and it’s syncing to the same Google account as Chrome on a Chrome OS/Windows/macOS device, then you’ll be able to use that phone as a security key. Just like a regular security key, if you lose the phone then you lose the credentials. More below.).

eSecurity Planet
JULY 7, 2023
Vulnerability scanning is critically important for identifying security flaws in hardware and software, but vulnerability scanning types are as varied as the IT environments they’re designed to protect. Agent-Server: The scanner installs agent software on the target host in an agent-server architecture.

The Last Watchdog
SEPTEMBER 30, 2019
2, another group of start-ups, flush with VC cash, is gaining ground with “homomorphic-like” technologies they claim have the same benefits as the purely homomorphic tools, but none of the performance penalties. Looking ahead, runtime will remain an integral part of any advancements made in cloud computing and machine learning.

Security Affairs
FEBRUARY 18, 2019
What a splendid job they have done for the cyber security community by bringing most of the key attack vectors under an organized framework that segregates these attack vectors in various stages of a typical attack. Pre-requisites: Sysmon logs from your environment A few apps. So, let us start with prerequisites. no big deal.

ForAllSecure
APRIL 4, 2023
Incident response in the cloud. James Campbell, CEO of Cado Security , shares his experience with traditional incident response, and how the cloud, with its elastic structure, able to spin up and spin down instances, is changing incident response. When log files are not all that detailed. And other hardware.

Thales Cloud Protection & Licensing
JANUARY 3, 2019
It changes the way you look at your business, improves your productivity and simplifies your life whether by helping you get home at night, buying groceries or deciding what to watch on any number of devices. Unfortunately, with every possibility a new security risk appears, and as a CISO you are well-aware of the implications.

OneHub
NOVEMBER 8, 2019
But we know working with enterprise businesses is much different than start-ups or small businesses. Whether you work with enterprise businesses exclusively, or are trying to make the switch, knowing how to share documents securely and safely is important. Types of Enterprise Files That Need to Be Shared Securely.

eSecurity Planet
DECEMBER 9, 2021
We make IT, security, or any business decision by weighing the risks and the rewards. Or as is often the case with security, what costs can we skip and still escape big penalties later? No one wants to go out of business because of sloppy preparation. Let’s start by defining the scope. Yet, it can get worse.

OneHub
MARCH 29, 2021
Often, the problem isn’t that they don’t want to participate; it’s that they’re busy, distracted, or overwhelmed. Onehub client portals improve customer engagement and collaboration. A client portal is a secure login area on your company’s website. Client portals keep business files secure.

The Last Watchdog
MAY 2, 2019
I often see a sizable gap between perceptions and reality among many SMB leaders,” Troy Gill a senior security analyst at AppRiver told me. I had the chance at RSA 2019 to discuss the SMB security landscape at length with Gill. Small and midsize businesses — so-called SMBs — face an acute risk of sustaining a crippling cyberattack.

The Texas Record
DECEMBER 5, 2019
How can your organization improve the way in handles public records requests to avoid lawsuits? Read through the presentation slides , or look over Snyder and Geddes’ nine recommendations below on how technological tools can improve and facilitate your public information request (PIR) program. Securing in the Cloud.

eSecurity Planet
OCTOBER 31, 2023
A pentest report should also outline the vulnerability scans and simulated cybersecurity attacks the pentester used to probe for weaknesses in an organization’s overall security stack or specific systems, such as websites, applications, networks, and cloud infrastructure.

The Texas Record
DECEMBER 5, 2019
How can your organization improve the way in handles public records requests to avoid lawsuits? Read through the presentation slides , or look over Snyder and Geddes’ nine recommendations below on how technological tools can improve and facilitate your public information request (PIR) program. Securing in the Cloud.

ForAllSecure
JUNE 16, 2021
APIs are vital in our mobile digital world, but the consequences of API security flaws have yet to be seen. During the pandemic sales of the Home Fitness cycle peloton grew massively, given its popularity, it's natural that security researchers would want to take a look. So how hard is it to hack APIs? Not very hard.

ForAllSecure
JUNE 16, 2021
APIs are vital in our mobile digital world, but the consequences of API security flaws have yet to be seen. During the pandemic sales of the Home Fitness cycle peloton grew massively, given its popularity, it's natural that security researchers would want to take a look. So how hard is it to hack APIs? Not very hard.

The Last Watchdog
MAY 24, 2023
Zero trust networking architecture (ZTNA) is a way of solving security challenges in a cloud-first world. The 4th Annual Multi-Cloud Conference and Workshop on ZTNA is an upcoming event for anyone interested in how the federal government is advancing standards in ZTNA. federal government or not. Let’s look at each of those five.

erwin
APRIL 4, 2022
In addition to our existing relational, cloud, big data DBMS and NoSQL targets, this release adds full support for six new NoSQL databases and one upgrade: Neo4j. If you’re a long-time erwin ® Data Modeler by Quest ® customer, you might be asking yourself, “What happened to the release naming convention of erwin Data Modeler?”

ForAllSecure
NOVEMBER 24, 2020
In this episode I talk about how Heartbleed (CVE 2014-0160) was found and also interview Rauli Kaksonen, someone who was at Codenomicon at the time of its discovery and is now a senior security specialist at the University of Oulu in Finland, about how new security tools are still needed to find the next big zero day. Apple Podcasts.

ForAllSecure
NOVEMBER 24, 2020
In this episode I talk about how Heartbleed (CVE 2014-0160) was found and also interview Rauli Kaksonen, someone who was at Codenomicon at the time of its discovery and is now a senior security specialist at the University of Oulu in Finland, about how new security tools are still needed to find the next big zero day. Apple Podcasts.
eSecurity Planet
NOVEMBER 10, 2023
Log monitoring is the process of analyzing log file data produced by applications, systems and devices to look for anomalous events that could signal cybersecurity, performance or other problems. Customer Loyalty and Trust: Effective log monitoring promotes an uninterrupted user experience, helping to ensure customer trust and loyalty.

ForAllSecure
NOVEMBER 24, 2020
In this episode I talk about how Heartbleed (CVE 2014-0160) was found and also interview Rauli Kaksonen, someone who was at Codenomicon at the time of its discovery and is now a senior security specialist at the University of Oulu in Finland, about how new security tools are still needed to find the next big zero day. Apple Podcasts.

eSecurity Planet
MAY 24, 2023
A cloud workload protection platform (CWPP) shields cloud workloads from a range of threats like malware, ransomware, DDoS attacks, cloud misconfigurations, insider threats, and data breaches.

ForAllSecure
JUNE 8, 2022
Vamosi: I once wrote about a petty car thief in Prague, Czech Republic who started the usual way by using scissors to cut the wires and hotwire the engine to drive away. But in the early 2000s, that was starting to give away to key fobs. So the car would start. Since then, car manufacturers have improved on this.

eSecurity Planet
OCTOBER 20, 2023
Hybrid cloud security is a framework for protecting data and applications in a computing environment that includes both private and public clouds. It combines on-premises and cloud-based resources to satisfy an organization’s diversified computing demands while ensuring strong security.

eSecurity Planet
OCTOBER 19, 2023
Private clouds avoid the shared environment of public cloud environments and thus are considered more secure, but users still need to take steps to get private cloud security right. Also read: Public Cloud Security Explained: Everything You Need to Know What is the Purpose of a Private Cloud?

The Last Watchdog
FEBRUARY 21, 2022
However, all is not lost if your healthcare organization is starting its cybersecurity journey, or even if you have a mature cybersecurity program. Start by assessing what critical information your organization needs to protect and maintain access to in order to provide services. Related: High-profile healthcare hacks in 2021.

The Last Watchdog
JULY 21, 2020
Cloud migration, obviously, is here to stay. But there’s no doubt that the exodus to a much greater dependency on hybrid cloud and multi-cloud resources – Infrastructure-as-a-Service ( IaaS ) and Platforms-as-a-Service ( PaaS ) – is in full swing. And now we have that same pattern playing out, once more, with cloud migration.

The Last Watchdog
SEPTEMBER 20, 2021
An array of promising security trends is in motion. New frameworks, like SASE , CWPP and CSPM , seek to weave security more robustly into the highly dynamic, intensely complex architecture of modern business networks. Now comes another security initiative worth noting. Security typically got bolted on, post-deployment.

eSecurity Planet
SEPTEMBER 25, 2023
The Cloudflare One SASE product builds off of the well-established global backbone that Cloudflare built for their content delivery and cloud security products. Founded in 2004, Cloudflare initially wanted to determine the source of email spam and became dedicated to building a better, more secure internet.

ForAllSecure
JANUARY 19, 2022
Is there something more secure? Simon Moffatt from CyberHut joins The Hacker Mind to discuss how identity and access management (IAM) is fundamental to everything we do online today, and why even multi-factor access, while an improvement, needs to yield to more effortless and more secure passwordless technology that’s coming soon.

Info Source
JUNE 28, 2022
I’ve taken the video transcript, not everyone wants to listen to the. DIR: Let’s get started, Kevin. DIR: Let’s get started, Kevin. Let’s start with the basics as you said. Last week, I posted updates about what the TWAIN Working Group is up to, and embedded the video below.
eSecurity Planet
JUNE 29, 2023
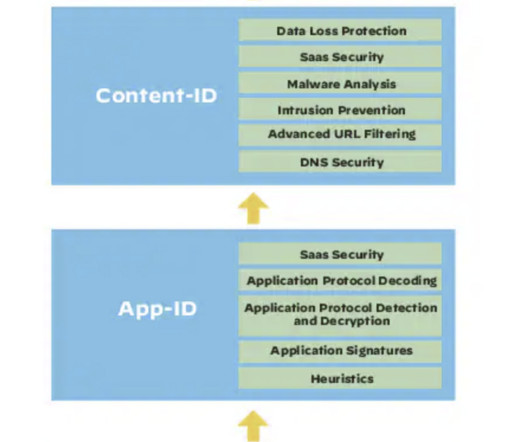
Enterprise security buyers might pay a premium for Palo Alto products, but they can typically buy with confidence. With nearly $7 billion in annual revenue and a 20%+ growth rate, Palo Alto (PANW) has the resources to stay competitive in the network security market.

Collaboration 2.0
SEPTEMBER 4, 2008
Google unplugs Windows Google decides that a security invasion from China was the last straw and bans the use of. Windows 7 Microsofts Windows 7 arrived in late 2009 and kicked off a PC upgrade cycle thats expected to. Hot Topics iPhone iPad Enterprise 2.0 Microsoft Office Green tech Smart phones Collaboration 2.0

eSecurity Planet
JANUARY 28, 2021
In fact, there remains a huge shortage of experienced security professionals available to fill open positions. A contributing factor to the cybersecurity skills gap is the large number of security startups that have been founded in recent years. As a result, security is expected to more than double in size to $300 billion by 2025.

Collaboration 2.0
SEPTEMBER 8, 2008
Google unplugs Windows Google decides that a security invasion from China was the last straw and bans the use of. An enterprise balancing act in the cloud By Oliver Marks | September 8, 2008, 11:24am PDT Summary Video of Dr Sukh Grewal talking about GE’s ‘Support Central’ environment at last week’s Office 2.0

eSecurity Planet
JANUARY 9, 2023
Vulnerability management tools go well beyond patch management and vulnerability scanning tools by discovering security flaws in network and cloud environments and prioritizing and applying fixes. Intruder has direct integrations with cloud providers and runs thousands of thorough checks. Heimdal Security. Visit website.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content