How we broke the cloud with two lines of code: the full story of ChaosDB
Security Affairs
NOVEMBER 12, 2021
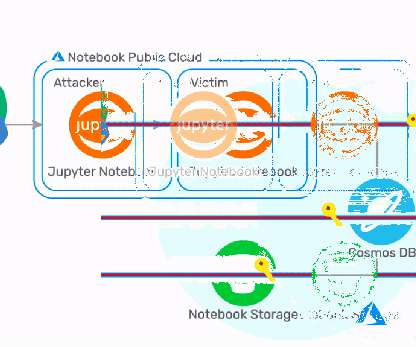
Wiz Research Team disclosed technical details about the discovery of the ChaosDB vulnerability in Azure Cosmos DB database solution. This vulnerability was so severe that we didn’t want to share the full extent of it until enough time had passed to properly mitigate it. This, however, was not the full story of ChaosDB.
















Let's personalize your content