Your Phone May Soon Replace Many of Your Passwords
Krebs on Security
MAY 7, 2022
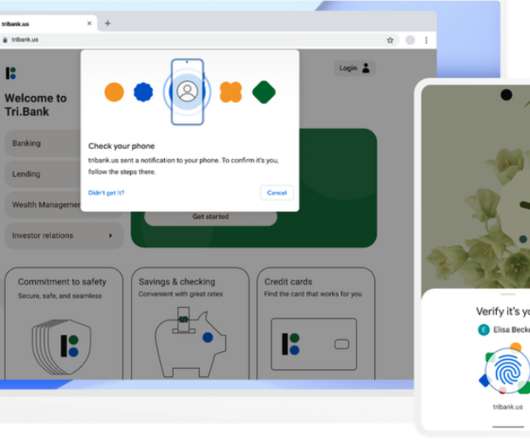
Apple , Google and Microsoft announced this week they will soon support an approach to authentication that avoids passwords altogether, and instead requires users to merely unlock their smartphones to sign in to websites or online services. Image: Blog.google.












































Let's personalize your content