51 Must-Know Phishing Statistics for 2023
IT Governance
JUNE 8, 2023
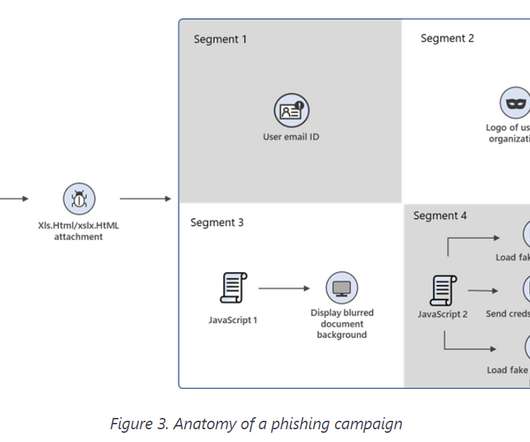
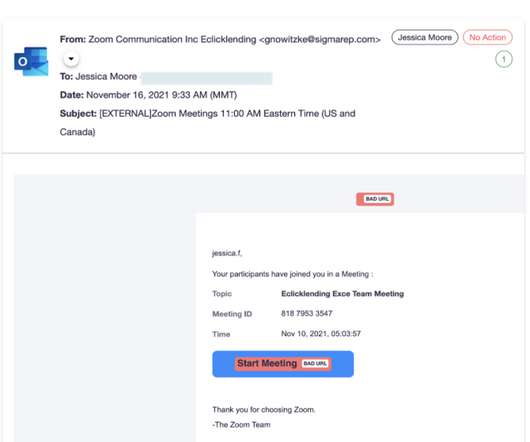
Phishing is one of the most common and dangerous forms of cyber crime. All it takes is a well-crafted email, social media post or phone message, and an employee who is too negligent or unaware to spot that its true nature. It’s why, in this blog, we’ve collected the most crucial phishing statistics you need to understand the threat.



















Let's personalize your content