Only big fines will change how the auditors audit
The Guardian Data Protection
JULY 9, 2019
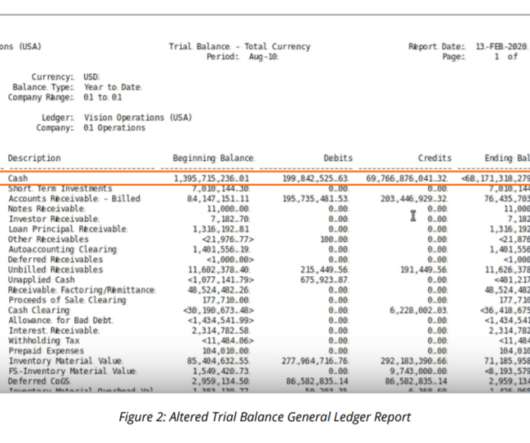
Splitting a firm’s audit and consulting functions has merit but only large penalties will affect proper change •Watchdog finds work of Patisserie Valerie auditor unacceptable This time last year the Financial Reporting Council tried to read the riot act to the auditing industry.
















































Let's personalize your content