Costa Rica May Be Pawn in Conti Ransomware Group’s Bid to Rebrand, Evade Sanctions
Krebs on Security
MAY 31, 2022
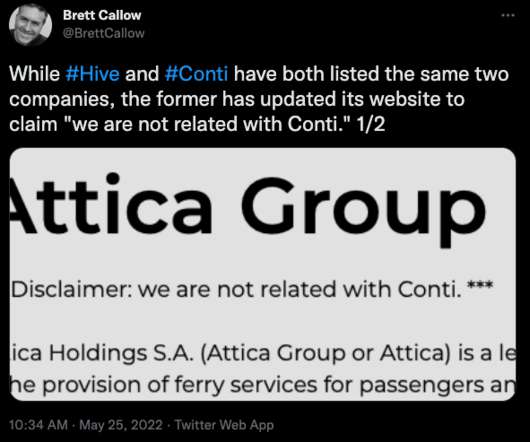
The intrusion comes just weeks after Costa Rican President Rodrigo Chaves declared a state of emergency in response to a data ransom attack from a different Russian ransomware gang — Conti. On May 20, Conti leaked more than 670 gigabytes of data taken from Costa Rican government servers.














Let's personalize your content