Is Your Chip Card Secure? Much Depends on Where You Bank
Krebs on Security
JULY 30, 2020
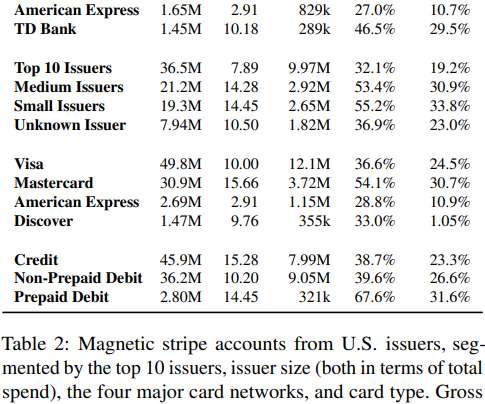
Chip-based credit and debit cards are designed to make it infeasible for skimming devices or malware to clone your card when you pay for something by dipping the chip instead of swiping the stripe. A chip-based credit card. But a recent series of malware attacks on U.S.-based Image: Wikipedia.


































Let's personalize your content