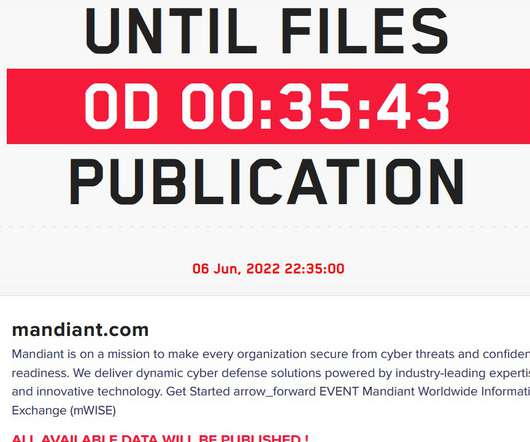
Lockbit ransomware gang claims to have hacked cybersecurity giant Mandiant
Security Affairs
JUNE 6, 2022
A Mandiant’s statement published by several websites states that the company was aware of the claims, but “at this point, we do not have any evidence to support their claims. Please vote for Security Affairs and Pierluigi Paganini in every category that includes them (e.g. ransomware to evade sanctions. Pierluigi Paganini.












































Let's personalize your content