Humans are Bad at URLs and Fonts Don’t Matter
Troy Hunt
OCTOBER 28, 2020
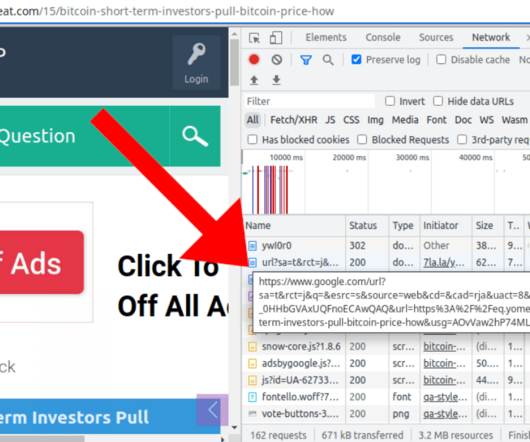
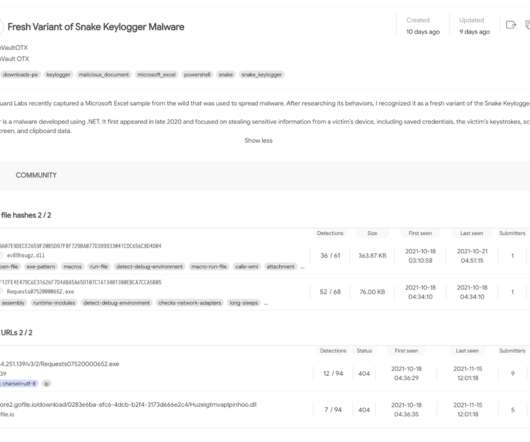
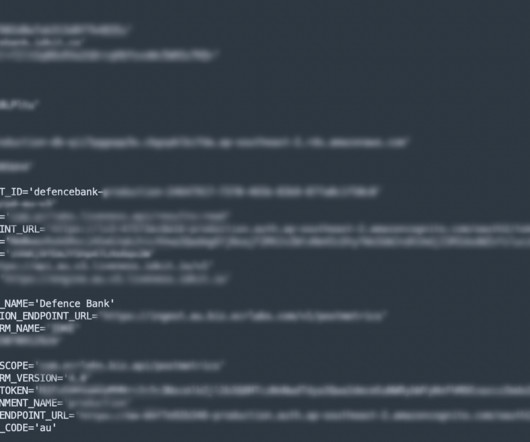
If I'm completely honest, I had no idea what the correct answer would be because frankly, I'm bad at reading URLs. Everything becomes clear(er) if I manually change the font in the browser dev tools to a serif version: The victim I was referring to in the opening of this blog post? That’s how [link] became [link]. — Bartek ?




































Let's personalize your content