Hiding Malware inside a model of a neural network
Security Affairs
JULY 26, 2021
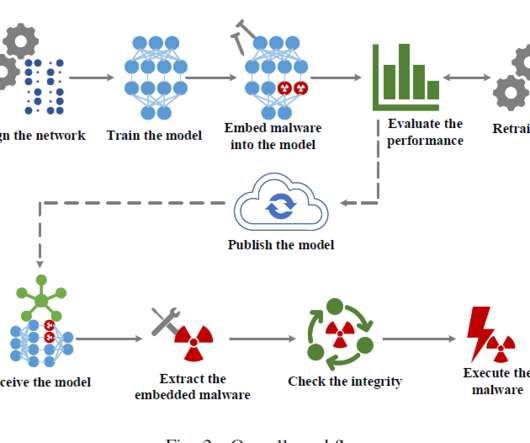
Researchers Zhi Wang, Chaoge Liu, and Xiang Cui presented a technique to deliver malware through neural network models to evade the detection without impacting the performance of the network. If the model doesn’t have enough neurons to embed malware, the attacker may opt to use an untrained model, which has extra neurons.














Let's personalize your content