Nation-State Attackers, Ransomware Groups Take Aim at Apache Log4j Flaw
eSecurity Planet
DECEMBER 15, 2021
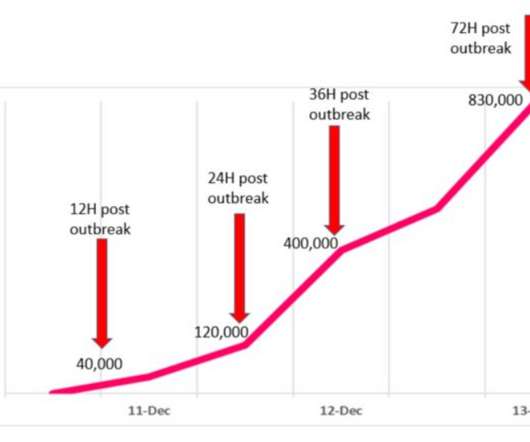
Security researchers at Check Point Software in a blog post said that after the first weaponized proof-of-concepts (POCs) illustrating the vulnerability hit the internet on Dec. Three days after the outbreak, we are summing up what we see until now, which is clearly a cyber pandemic that hasn’t seen its peak yet,” they wrote.















Let's personalize your content