Supply Chain Flaws Found in Python Package Repository
eSecurity Planet
AUGUST 3, 2021
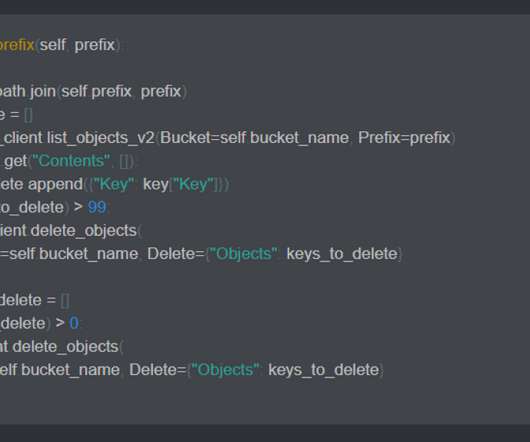
Administrators overseeing the Python Package Index (PyPI) in recent days found themselves responding to vulnerabilities found in the repository of open source software, the latest security problems to hit the Python community. As I’ve mentioned several times before, some supply chains have critical vulnerabilities.































Let's personalize your content