New LockFile ransomware gang uses ProxyShell and PetitPotam exploits
Security Affairs
AUGUST 21, 2021
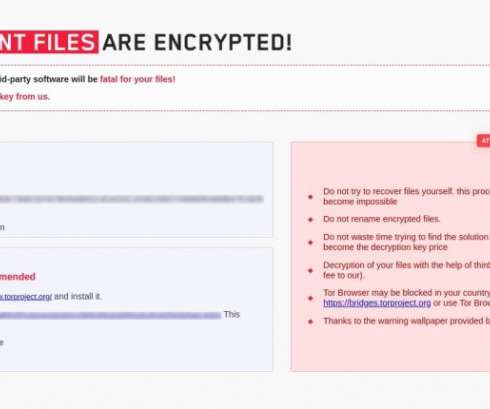
The vulnerabilities are exploited remotely through Microsoft Exchange’s Client Access Service (CAS) running on port 443 in IIS. It is not clear how the attackers gain initial access to the Microsoft Exchange Servers.” Once encrypted the files, the ransomware will append the .lockfile











Let's personalize your content