GUEST ESSAY: Best practices to shrink the ever-present risk of Exchange Server getting corrupted
The Last Watchdog
FEBRUARY 5, 2024
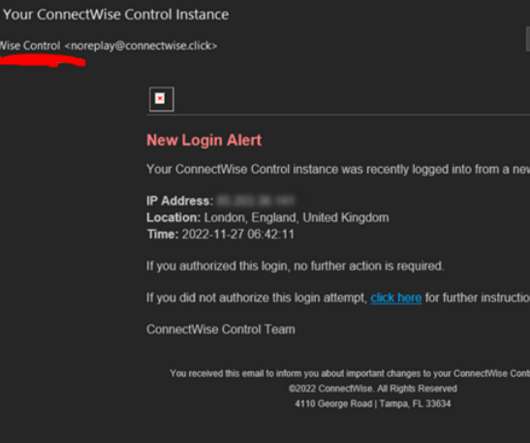
Exchange server ordeal Take what recently happened to iConnect Consulting , a San Francisco-based supplier of Laboratory Information Management System ( LIMs ) consulting services. The user interface is intuitive, making it accessible for users with varying levels of technical expertise. Robust access control. Backup strategies.







































Let's personalize your content