TroyStealer – A new info stealer targeting Portuguese Internet users
Security Affairs
JUNE 13, 2020
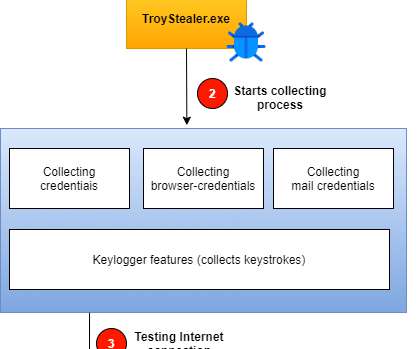
To keep your system safe, one of the things you can do is following a cyber doctrine focused on the threats that lunk on the web. cc @CNCSgovpt @sirpedrotavares pic.twitter.com/1bDK3BtYeE — abuse.ch (@abuse_ch) June 12, 2020. In detail, the malware detects if it is running inside a VM and stops the execution.

























Let's personalize your content