Prometei botnet is targeting ProxyLogon Microsoft Exchange flaws
Security Affairs
APRIL 26, 2021
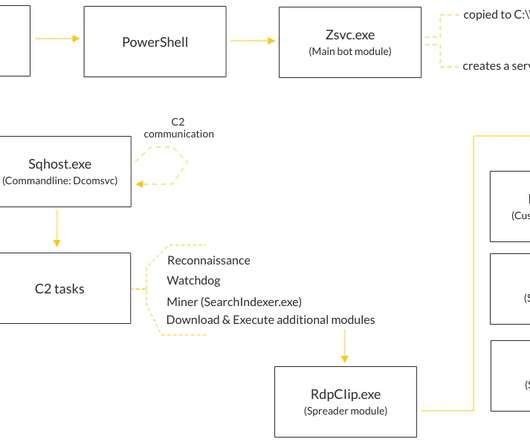
A deep investigation on artifacts uploaded on VirusTotal allowed the experts to determine that the botnet may have been active at least since May 2016. The crypto-mining has a modular structure and employes multiple techniques to infect systems and evade detection. ” reads the analysis published by Cybereason.



















Let's personalize your content