HackerGPT, first launched in 2023, is a ChatGPT-powered tool that merges AI technology with cybersecurity-focused expertise. Now, with the beta release of HackerGPT 2.0 in February 2024, it serves as an extensive repository of hacking tools and techniques to actively assist users in managing complex cybersecurity protection strategies. It uses advanced natural language processing to provide insights into both offensive and defensive cyber activities.
What distinguishes HackerGPT from other tools is its ability to deliver actionable insights for different types of query functions. From analyzing attack methods and suggesting defense tactics to doing vulnerability assessments, it provides users with the knowledge to improve their security posture.
HackerGPT collaborates with WhiteRabbitNeo to offer comprehensive AI assistance. The free subscription offers access to the WhiteRabbitNeo 33B parameter model, a fine-tuned version of LLaMA 2, with a restriction of 50 usage per day. The Pro plan costs $20 per month and includes a higher usage limit.
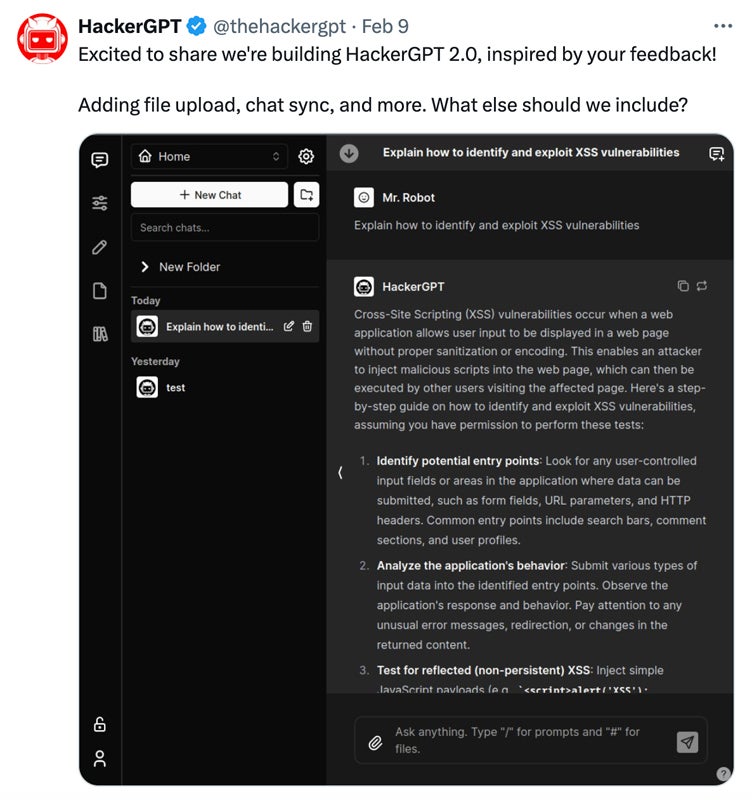
Table of Contents
Featured Partners: AI Software
Purpose of HackerGPT
HackerGPT adds to the set of AI technologies available to the cybersecurity community. While other AI-based systems, such as OSINVGPT, PentestGPT, WormGPT, and BurpGPT, perform various types of cybersecurity tasks, HackerGPT is designed particularly for ethical hacking practices.
This means that it can only generate responses that follow ethical norms and legal boundaries, guaranteeing that its users engage in responsible and lawful behavior. Aside from ethical hacking, HackerGPT seeks to assist professionals and improve security assessments.
This model attempts to help users with both offensive and defensive cybersecurity responsibilities. It provides extensive insights into cybersecurity topics to guide users through offensive strategies like Wi-Fi network attacks using specialized tools. It also teaches defensive strategies and promotes safe practices and awareness.
How HackerGPT Works
HackerGPT claims to prioritize data security by delivering queries to OpenAI or OpenRouter while ensuring user privacy in the process. It has an intuitive UI similar to ChatGPT. It promotes active input from users and includes clear instructions for configuring local or hosted instances. With swift response capabilities, GPT-3 and GPT-4 capacity, and upcoming mobile access, HackerGPT provides accessibility on most platforms, plus operational efficiency.
The successful facilitation of responses generally includes these seven steps:
Step 1: User Query
A user interacts with the tool by entering a cybersecurity-related command or query. This interaction is usually done using a web browser or a particular interface supplied by HackerGPT. It uses ’embedding’ technology to comb through its archive of hacking data and give complete responses suited to the user’s inquiry.
Step 2: Query Verification
When HackerGPT receives the user’s query, it verifies the user’s identification and manages any query restrictions associated with the account. This differs for free and premium users. This stage also verifies that the user’s query complies with the platform’s usage guidelines and limitations.
Step 3: Database Check
After confirming the query, HackerGPT explores its extensive library of cybersecurity expertise and resources to find information and resources relevant to the user’s inquiry. The database provides a variety of information, including hacking tools and best practices.
Step 4: Translation
If the user’s query is in a language other than English, HackerGPT may apply translation technologies to convert it into English before performing the database search. This is to ensure that the search results are correct and relevant to the user’s query. However, this function may be limited depending on the plan.
Step 5: Response Generation
Once an appropriate match is located in the database, HackerGPT delivers a response that is specific to the user’s inquiry. The response may include thorough explanations, step-by-step instructions, code snippets, or additional relevant material in order to successfully handle the user’s query.
Step 6: Secure Data Transmission
Before sending the response to the user, HackerGPT securely examines the query and response, ensuring that no personal or sensitive information is contained in the transmission. This helps to preserve the user’s privacy and security when using the platform.
Step 7: Response Delivery
Finally, HackerGPT drops the generated response to the user via the interface or platform utilized for interaction. The user may then examine the results, access any supplied resources or instructions, and act on the information provided by HackerGPT.
Query Functions in HackerGPT
HackerGPT provides a range of query functions such as network hacking, mobile hacking, payload creation, attack vector analysis, and vulnerability assessment. However, users may require some level of knowledge depending on their query to fully utilize its capabilities effectively.
Here are the five query functions you can use:
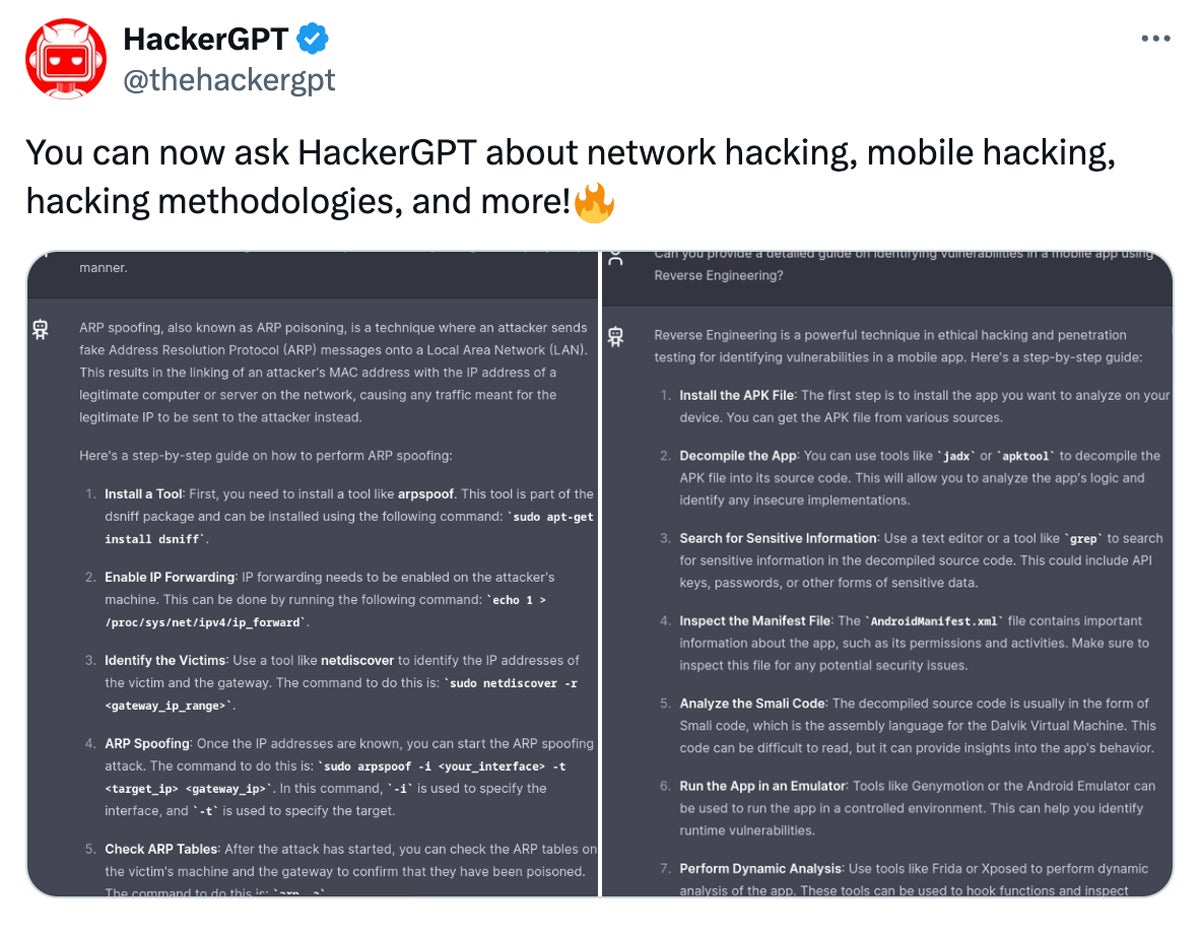
- Network hacking: This function allows users to delve into network security, offering information about computer network vulnerabilities and threats. It discusses techniques like port scanning, packet sniffing, and exploiting flaws in network protocols.
- Mobile hacking: This feature allows users to investigate vulnerabilities particular to mobile devices, such as smartphones and tablets. It includes techniques like jailbreaking, rooting, and exploiting flaws in mobile apps and operating systems.
- Payload creation: Users can generate payloads, which are malicious malware or scripts intended to exploit vulnerabilities in target systems. Users can design payloads for specific attack situations, such as remote code execution or privilege escalation.
- Attack vector analysis: This query function allows users to assess pathways or methods used by attackers to obtain unauthorized access to systems or data. It also teaches users about social engineering, phishing, and brute force attacks.
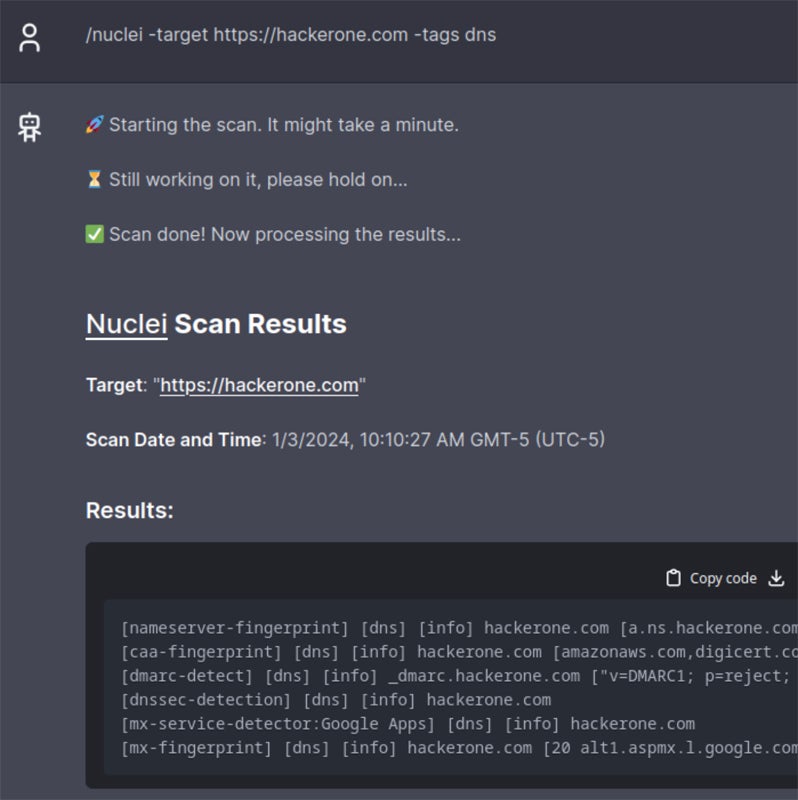
- Vulnerability assessment: HackerGPT makes it easier to analyze vulnerabilities by offering instructions on how to discover, prioritize, and mitigate security flaws. Users can do extensive vulnerability assessments to improve their system security.
Integration with Plug-ins
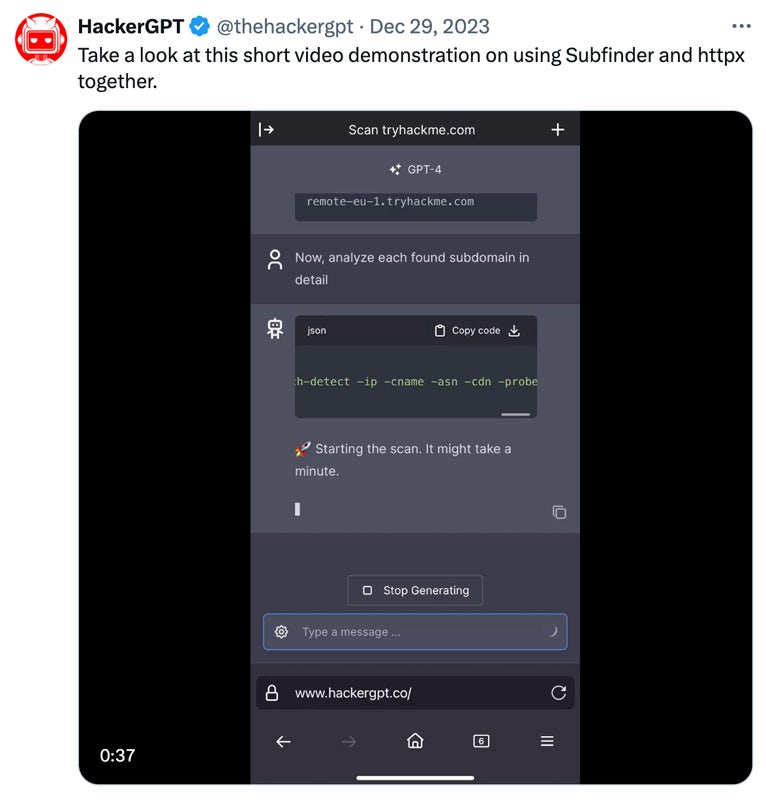
HackerGPT integrates with a variety of plug-in tools to improve its capabilities. CyberChef allows you to encode and decode data, hash passwords, analyze traffic, and convert data formats. GAU (GitHub Actions Utilities) provides tools to manage GitHub workflows, automate software development operations, and integrate security testing. Subfinder, a command-line utility, identifies subdomains and helps detect potential network entry points.
Implications in Cybersecurity
HackerGPT plays a role in enhancing cybersecurity capabilities — from ethical hacking, specialized cyber-assistant, to training and education. Its proper usage could result in a safer digital environment.
Ethical Hacking
HackerGPT encourages the ethical use of hacking expertise for lawful purposes, particularly in discovering and fixing security weaknesses. Its creators emphasize its adherence to ethical, ‘white-hat’ hacking ideals, preferring defensive acts such as vulnerability resolution above exploitative approaches.
HackerGPT entails understanding how to bypass lock screens or exploit software defects for ethical motives. However, demonstrating mobile hacking without appropriate authority or a passcode sets up ethical and legal concerns. It’s critical for HackerGPT to emphasize responsible use, namely for security research and ethical hacking, while also respecting privacy and data protection regulations and understanding legal implications.
Cyber-AI Assistant
HackerGPT responds quickly to user queries, allowing for more timely decision-making during cybersecurity events. Similar to ChatGPT’s capability, this approach provides instant analysis of attacks, providing insights and solutions as they occur. Its fast recommendations and solutions allow for timely threat mitigation, minimizing any possible damage in cyber incidents.
Training & Education
HackerGPT serves as a cyber-repository and educational resource for cybersecurity training programs, assisting students in learning complex ideas interactively. Its thorough coverage of topics promotes skill development and provides practical learning opportunities. Through simulated real-world scenarios, it provides students and professionals with hands-on experience, effectively preparing them for real-world cybersecurity scenarios.
Challenges & Limitations
While HackerGPT offers numerous benefits to the cybersecurity community, it also poses several challenges and limitations:
- Potential misuse: There is a possibility that users will use HackerGPT for unethical purposes, thus demanding tight tracking of the system to prevent misuse.
- False sense of security: Over-reliance on HackerGPT may cause users to neglect the importance of human expertise and validation of its recommendations.
- Insufficient understanding: Users with lacking cybersecurity knowledge may fail to completely comprehend HackerGPT’s instructions, prompting additional instructional efforts.
- No real-time access: This limits HackerGPT’s capacity to personalize response to specific targets or situations.
- Accuracy and reliability concerns: Despite efforts to provide dependable guidance, inaccuracies and obsolete information may occasionally occur, reducing HackerGPT’s efficacy.
- Regulatory compliance: Organizations must ensure HackerGPT usage complies with data protection and security requirements, which necessitates explicit guidelines and controls.
- Compatibility issues: Integrating HackerGPT into existing frameworks may present technological issues that require careful planning, decision-making, and implementation to ensure compatibility with other security tools.
Addressing these challenges requires a balanced strategy that includes strong training and education programs, careful adherence to ethical principles, ongoing monitoring and validation of HackerGPT’s feedback, and collaboration between human professionals and AI systems.
HackerGPT is a newly designed tool, and its full range of functionality and possible applications have yet to be fully explored. While initial impressions indicate that it has promise for effectively assisting various cybersecurity tasks, we still need more investigation and testing to determine its exact capabilities and limitations.
While HackerGPT can aid in preemptive measures and offer insights during security operations, it’d be best to develop and maintain a comprehensive incident response plan that ensures swift and effective actions when breaches or threats occur.








