A newly discovered campaign pushing malicious open source software packages is designed to steal mnemonic phrases used to recover lost or destroyed crypto wallets, according to a report by ReversingLabs. *
The campaign, dubbed BIPClip was uncovered in early March and targets developers working on crypto-related projects. In all, seven different open source packages were identified with links to the campaign, encompassing 19 different file versions. The malicious packages in question target developers who are implementing the Bitcoin Improvement Proposal 39, or BIP39, a list easy-to-remember words that are used to generate a binary seed used to creates deterministic BitCoin wallets, according to a blog post by ReversingLabs researcher Karlo Zanki.
Malicious Open Source Dependencies At Work
The campaign first came to light after one of the packages, bip39_mnemonic_decrypt, turned up in a scan of the Python Package Index (PyPI) using ReversingLabs Spectra Assure software supply chain security platform. The package contained a number of suspicious characteristics including features that performed Base64 decoding as well as a common open source library, requests, that is used for network communication within the Python ecosystem.
Further investigation revealed that the bip39_mnemonic_decrypt was a dependency of a second package, mnemonic_to_address, which could be used to create a seed from the user’s secret mnemonic seed phrase and was free of malicious functionality. Both packages were published in early February by james_pycode, a throwaway PyPI maintainer account that was created on the same day as the packages were published.
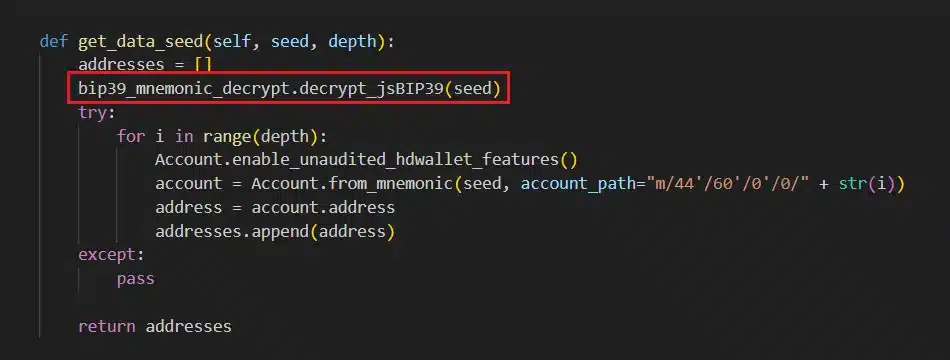
At the heart of the campaign is a malicious function, decrypt_jsBIP39, which was found in the bip39_mnemonic_decrypt package at the very end of the __init__.py file. The decrypt_jsBIP39 function is listed after several, non-malicious functions that are not actually used in the code base, an apparent effort to throw off developers or security teams hunting for red flags in the open source library.
When run, the function decodes the Base64 encoded URL of the data exfiltration server and invokes another function named cli_keccak256, a malicious function the name of which invokes keccak256, a legitimate cryptographic hash function commonly used to compute the hashes of Ethereum addresses, transaction IDs, and other important values in the Ethereum ecosystem.
More Packages, More Malicious Dependencies
More digging by Zanki and ReversingLabs turned up another malicious Python file pair with nearly identical code: public-address-generator and erc20-scanner, which were also published from a throwaway PyPI account on March 1st. This second file pair appear to work together in the same way as the mnemonic_to_address and bip39_mnemonic_decrypt pair, with malicious functionality identical to that found in the bip39_mnemonic_decrypt package is implemented in the erc20-scanner package. The second set of packages also use the same command and control (C2) server to exfiltrate stolen mnemonics as the first pair, reinforcing their connection.
Hashdecrypt(s): evidence of an older campaign
Finally, Zanki and ReversingLabs uncovered another malicious package, hashdecrypts, that uses slightly different methods to exfiltrate mnemonic phrases than the other packages connected to the BIPClip campaign, and suggests a much longer running campaign targeting mnemonic recovery phrases.
The newly discovered malicious Python package, hashdecrypts, was published on March 1st by a PyPI user account, luislindao. Unlike the other packages, however, this wasn’t a new, throwaway account. Luislindao was first registered on PyPI in August 2019. However, the code contained in hashdecrypts was almost identical to the malicious code found in the bip39_mnemonic_decrypt and erc20-scanner packages, suggesting a connection to the BIPClip campaign.
When run, hashdecrypts places an HTTP GET request to a Base64 encoded URL from which it retrieves the address of the C2 server. The package then sends data to that address using a HTTP POST request. Inside the hashdecrypts code there is a comment header pointing to a github repository belonging to the HashSnake Github user account. When Zanki looked at the commit history for the linked HashSnake Github repository he found a related file, hashdecrypt (note: no trailing “s”), that was first published on December 4, 2022. All three published versions of that package contained the same malicious functionality and fetched the same command and control (C2) server address from the same GitHub repository.
Uptake of the newly posted malicious PyPI packages was small – with 997 downloads of the public-address-generator package, 341 of the erc20-scanner package, and 224 of the hashdecrypts package. That suggests the campaign had a limited reach.
That’s not so true of the older hashdecrypt package, where ReversingLabs reported 4,295 downloads dating back to December, 2022.
Crypto in the crosshairs (again)
The BIPClip campaign underscores the continued targeting of cryptocurrency related applications and code by malicious actors, according to ReversingLabs. Both cyber criminal and nation state hacking groups have taken an interest in exploiting cryptocurrency software and infrastructure, with the goal of stealing the content of cryptocurrency wallets.
Recent campaigns include the compromise of the open source Ledger Connect Kit, resulting in the redirection of crypto transactions; to publication of malicious npm packages related to cryptocurrency applications and platforms. Nation state actors affiliated with the Democratic Republic of North Korea (DPRK), for example, are believed to have stolen as much as $3 billion in cryptocurrency in the past five years. Stolen cryptocurrency now accounts for as much as 5% of North Korea’s GDP.
That context puts additional burden on developers working on crypto-related projects to assess the security of the open source and commercial code used in their development pipeline, and to assess the security of software artifacts both before, during and after the development and build process, ReversingLabs said.
(*) Editor’s note: In addition to my work as Editor in Chief at The Security Ledger, I am a salaried employee at ReversingLabs where I have served as the Cyber Content Lead since November 2021.


Pingback: Malicious Python Packages Target Crypto Wallet Recovery Passwords - F1TYM1
Pingback: March 15 | cybersecurity update
it’s possible to recover stolen bitcoin or romantic dating funds by DragonWebRecovery
If you have been the victim of Crypto theft, it’s important to report it to DragonWebRecovery. I am writing this testimony to share my incredible experience of recovering my lost cryptocurrency with the assistance of a skilled DragonWebRecovery. I had invested a significant amount of money in cryptocurrency, believing in its potential for growth and financial security. However, due to a technical issue with my wallet or a security breach that I was unaware of, I suddenly found myself unable to access my funds. Panic and despair set in as I realized the gravity of the situation. In my search for a solution, I came across DragonWebRecovery reputable and trusted hacker known for their expertise in cybersecurity and digital forensics. With nothing to lose and everything to gain, I decided to reach out to them for help. DragonWebRecovery responded promptly and professionally! After a series of carefully executed procedures and security measures, [ DragonWebRecovery ] successfully recovered my cryptocurrency and restored all my bitcoins to my wallet.
If you ever find yourself in a similar situation, I wholeheartedly recommend reaching out to DragonWebRecovery for assistance. Their expertise and commitment to helping others are truly commendable, and I am living proof of the positive impact they can have on someone’s life. Via Email – info@dragonwebrecovery.com
Losing $294,000 worth of bitcoin to a romance scam is devastating. It’s a stark reminder of the risks lurking in the digital world. However, it’s heartening to hear that you found assistance from Mighty Hacker Recovery. Their swift action and expertise in recovering your stolen funds demonstrate the value of having reliable support in such situations. Your story underscores the importance of vigilance online and seeking trusted professionals when faced with cybercrime. If anyone else finds themselves in similar distress, it’s reassuring to know there are reputable resources like Mighty Hacker Recovery available to help.
www . mightyhackerrecovery . com
support (at) mightyhackerrecovery . com
Whats App + 1 ( 4 2 5 ) – 2 0 9 – 5 7 6 1
ɪꜰ ʏᴏᴜ’ᴠᴇ ʙᴇᴇɴ ꜱᴄᴀᴍᴍᴇᴅ ɪ ꜱᴜɢɢᴇꜱᴛ ʏᴏᴜ ꜱʜᴏᴜʟᴅ ꜰɪʀꜱᴛ ɢᴀᴛʜᴇʀ ᴀʟʟ ᴛʜᴇ ᴇᴠɪᴅᴇɴᴄᴇ ᴀɴᴅ ᴄᴏɴᴛᴀᴄᴛ ᴀ ʀᴇᴄᴏᴠᴇʀʏ ꜱᴘᴇᴄɪᴀʟɪꜱᴛ. ɪɴ ᴍʏ ᴄᴀꜱᴇ, ᴛʜᴇ ᴘʀᴏᴄᴇꜱꜱ ᴛᴏᴏᴋ 24 ʜᴏᴜʀꜱ . ɪ ᴡᴀꜱ ᴀʙʟᴇ ᴛᴏ ɢᴇᴛ ʙᴀᴄᴋ ᴀ ꜱᴜʙꜱᴛᴀɴᴛɪᴀʟ ᴀᴍᴏᴜɴᴛ ᴏꜰ ᴛʜᴇ ᴍᴏɴᴇʏ ʟᴏꜱᴛ, ᴍᴀʏ ɪ ꜱᴜɢɢᴇꜱᴛ ꜱᴄᴀᴍ ʀᴇᴄᴏᴠᴇʀʏ ꜱɪᴛᴇ. ᴛʜᴇʏ ʜᴇʟᴘᴇᴅ ᴍᴇ ʀᴇᴄᴏᴠᴇʀ ᴍʏ ꜰᴜɴᴅꜱ ᴡɪᴛʜ ɢᴏᴏᴅ ᴄᴏᴜɴꜱᴇʟʟɪɴɢ ᴀɴᴅ ꜰɪɴᴀɴᴄɪᴀʟ ꜱᴜᴘᴘᴏʀᴛ ꜱʏꜱᴛᴇᴍ ᴛʜᴀᴛ ᴄᴀɴ ʜᴇʟᴘ ʏᴏᴜ ᴀᴛ ᴛʜɪꜱ ᴅɪꜰꜰɪᴄᴜʟᴛ ᴛɪᴍᴇ. ɪꜰ ʏᴏᴜ ʜᴀᴠᴇ ʙᴇᴇɴ ᴀ ᴠɪᴄᴛɪᴍ ᴛᴏ ɪɴᴛᴇʀɴᴇᴛ ʀᴇʟᴀᴛᴇᴅ ꜰʀᴀᴜᴅꜱ ᴅᴏ ɴᴏᴛ ʜᴇꜱɪᴛᴀᴛᴇ ᴛᴏ ʀᴇᴀᴄʜ ᴏᴜᴛ ᴛᴏ moooredavid393@gamil.com
—ᴛʜᴇʏ’ʀᴇ ʀᴇʟɪᴀʙʟᴇ.
Big thanks to Mrs Evelyn Rayn one of the best BINARY OPTION, FOREX AND BITCOIN manager who has the best strategy and signals that can help you win every time you trade .. before meeting her I was scammed several times and I lost $20000 to 2 different managers who claims they are real but turn into monsters the moment I fund my trading account … but today I’m so grateful to Mrs Evelyn Rayn for coming to my rescue .. I posted this to those who are already given on binary and Forex options and to the newbies take advice and be saved.. if you contact her tell her I referred you to her so that I will have my referring bonus….you can contact her via email: Evelynrayn6@gmail.com or WhatsApp +1 (945) 7130 792
HOW TO RECOVER YOUR STOLEN CRYPTO’S 2024
MY CRYPTO RECOVERY EXPERIENCE 2024 WARNING: Scammers will stop at nothing to steal your hard-earned money! But, I’m living proof that JETWEBHACKERS can help you RECLAIM YOUR LOST FUNDS! I thought I’d lost my life savings of $58,000 after investing with a fake broker, promising me a whopping $187,000 profit to fund my urgent surgery. But, JETWEBHACKERS didn’t give up on me. They worked tirelessly to track down my money and recover it. And, after months of intense effort, they successfully recovered my entire investment – $58,000! I’m now able to focus on my health and recovery, knowing that I’ve been given a second chance thanks to JETWEBHACKERS. Don’t let scammers ruin your life like they almost did mine! If you’re in a similar situation, don’t hesitate to reach out to JETWEBHACKERS. They’ll be your champion in the fight against online fraud!” CONTACT THEM VIA EMAIL:jetwebhackers @ gmail .com TELEGRAM: @jetwebhackers