Cloud configuration management runs and regulates cloud configuration settings, parameters, and policies to streamline cloud services and assure security. This includes maintaining changes in virtual machines, storage resources, networks, and applications. Configuration management guarantees that enterprises maintain security and compliance while streamlining operations via automation and centralized control of their whole infrastructure environment.
This guide covers the importance of cloud configuration management, its main components, security benefits, challenges, and best practices.
Table of Contents
Why Cloud Configuration Management Is Important for Security
Cloud configuration management is vital for security due to:
- Complex cloud environment: The dynamic nature of cloud services contributes to the likelihood of misconfigurations, exposing security risks that may be reduced by good management.
- Public accessibility: Because cloud resources are by default public, limited access to sensitive data is required, highlighting the significance of secure setups for data security.
- New technologies: The emergence of serverless computing, containers, and microservices creates new security concerns that need precise setup for effective protection.
- Compliance requirements: Stringent rules require meticulous configuration control, highlighting the need for cloud resources to adhere to specified security standards.
- Identity and access management: IAM controls are critical to ensuring that only authorized persons or systems have access to resources, emphasizing the need for secure settings in identity and access management.
Main Components of Cloud Configuration Management
Cloud configuration management comprises a wide range of components that work together to define, provide, and maintain the intended state of cloud resources and applications in a consistent and automated way. Here are its main components:
- Cloud computing platform: The service provider impacts the available configuration tools and services, each with its own APIs and administration tools.
- Cloud deployment model: Public, private, and hybrid deployments all have different configuration requirements; private clouds may demand more stringent security, affecting settings, whereas hybrid setups handle both on-premises and cloud configurations.
- Cloud network configurations: Networking settings, subnets, firewalls, and routing configurations are critical for successful communication between cloud services and are handled by configuration tools to align with the desired state.
- Cloud compute configurations: Virtual machines, server settings, and application configurations are developed and maintained consistently using configuration tools, ensuring that requirements such as size, storage, OS, and application parameters correspond to the desired state.
- Cloud storage settings: Configuration management establishes data storage, access permissions, and backup rules, allowing tools to manage storage settings consistently and regularly.
- Cloud security policies: It is essential to establish and enforce security policies, which include rules, access restrictions, and encryption settings, with configuration tools that align these configurations with corporate security standards.
- Cloud security configurations: Configuration tools for cloud security implement best security practices and secure defaults, ensuring services are safely configured by default and any deviations from the secure setups are quickly identified and remediated.
- Cloud deployment and migration path: Configuration management solutions simplify deployment by supplying resources according to a defined plan and maintaining configurations throughout the migration of existing systems to the cloud.
10 Security Benefits of Cloud Configuration Management
Cloud configuration management is an essential process in cloud infrastructure security, providing tools to strengthen defenses, ensure compliance, and respond to events. These benefits help enterprises successfully navigate the cloud, protect data, and sustain trust among stakeholders:
- It enables effective access control management. Effective configuration management enables precise control over access permits and privileges. Fine-grained access controls reduce the risk of illegal access by ensuring that only authorized people have the required permissions.
- It allows accountability and provides an audit trail. Configuration management technologies give audit trails, allowing for change monitoring and accountability for configuration changes. An audit trail improves openness, assists forensic investigation, and holds persons accountable for prohibited or improper modifications.
- It provides automated security controls. Using automated configuration management to implement security controls guarantees that security measures are consistently applied. Automated security controls lower the risk of manual oversight, enforce rules systematically, and keep the environment secure and compliant.
- It enforces encryption policy. Encryption policy enforcement assures protection of data in transit and at rest while also resolving confidentiality concerns and adhering to security best practices.
- It improves security posture. Identifying and correcting misconfigurations minimizes vulnerability to security flaws, assaults, and data breaches.
- It supports incident response planning. Configuration management supports incident response planning through providing an overall view of the condition of the environment. With a well-documented and frequently updated configuration state, incident response teams can act quickly and effectively during security issues.
- It increases compliance. Ensuring that cloud configurations adhere to security standards helps businesses meet regulatory obligations (for example, GDPR, SOX, ISO27001) and pass compliance audits.
- It provides rapid detection and response. Continuous configuration monitoring allows quick identification of security problems and prompt response. It reduces the likelihood of damage while helping maintain a secure operational environment.
- It implements secure defaults. Enforcing secure defaults through configuration management guarantees that resources are supplied with a minimum level of security. Secure defaults decrease the attack surface and lay the groundwork for secure setups from the start, minimizing possible risks.
- It quickly remediates vulnerability. Automated configuration management tools can detect and remediate vulnerabilities. A quick vulnerability fix decreases the window of opportunity for attackers and strengthens the cloud environment’s security posture.
10 Cloud Configuration Management Challenges
Navigating the complexities of cloud configuration management poses several challenges, ranging from compliance issues to security risks. Addressing these issues is critical for efficient cloud operations:
- Complexity: The dynamic and changeable nature of cloud systems can lead to complex configurations, resulting in deployment failures.
- Managing multi-cloud and hybrid cloud settings: Managing configurations across various cloud providers or hybrid setups adds complexity and possible expenses. Coordination and consistency become more difficult, necessitating the use of specialized resources and methods.
- Cost: Overprovisioning resources or misconfigurations might result in unanticipated expenses. Inadequate resource management can result in financial inefficiencies and budget overruns.
- Lack of native tools: While cloud services’ native tools may provide basic functionality, they may be insufficient for solving complex setup requirements. To properly achieve certain configuration needs, businesses may need to invest in additional third-party tools.
- Human error: Misconfigurations caused by manual human input can pose security risks and operational issues. Human configuration mistakes can result in security breaches, service outages, and increased operational hazards.
- Inadequate deployment planning: During the deployment phase, lack of preparation can lead to configuration management issues and project failure. Poorly planned deployments can lead to high costs, operational inefficiencies, and organizational discontent.
- Scalability issues: This may occur as the company expands and requires changes to setups and deployment methodologies. Failure to handle scalability concerns may cause performance bottlenecks and stifle business growth.
- Inconsistent change management: A lack of a consistent change management approach might result in untracked or unapproved configuration changes. Inconsistent change management can cause configuration drift, making it difficult to maintain a stable and safe system.
- Limited visibility: A lack of insight into the configuration state might impede efficient monitoring and troubleshooting. Difficulties discovering and correcting configuration errors can lead to extended downtime and increased security threats.
- Ensuring compliance: Ensuring that configurations meet regulatory standards can be difficult, particularly in highly regulated businesses. Noncompliance may result in legal implications, fines, and reputational harm to the company.
10 Cloud Configuration Best Practices
To ensure effective cloud configuration management, consider the following best practices:
- Use IaC (Infrastructure as Code). Store configuration settings in version control, use IaC, and conduct code reviews for automated deployments to ensure versioning and consistency.
- Employ purpose-built tools. To optimize for the cloud environment, use cloud-specific tools to implement access restrictions and security regulations.
- Adhere to the principle of least privilege. Reduce access and permissions to the bare minimum for each position or user to improve security posture.
- Automate. Use automation and orchestration to minimize manual configuration activities and ensure deployment efficiency and consistency.
- Train and upskill employees. Invest in training to ensure that your staff knows cloud setups, security best practices, and applicable technologies.
- Conduct regular audits. Review and audit configurations on a regular basis to guarantee continuous security and compliance, identifying and correcting any potential vulnerabilities.
- Use free and open-source tools. Consider using open-source cloud security posture management (CSPM) tools in multi-cloud and hybrid settings to increase flexibility and cost-effectiveness.
- Properly execute cloud deployment plan. For effective deployment, create and maintain baselines, employ automation tools, record difficulties, and adhere to cloud service providers’ tools.
- Create and analyze the test plan. Test common infrastructure components, code in lower environments, confirm data integrity, validate load balancer setups, and run disaster recovery scenarios.
- Analyze test results. Consider success factors, document test conditions, compare performance data to baselines, check performance for specific scenarios, and guarantee SLA compliance, all of which contribute to a dependable and optimal cloud configuration.
Also see:
- Top 7 Cloud Security Posture Management (CSPM) Tools [2023]
- CNAP Platforms: The All-in-One Solution for Cloud Security
Top 3 Tools for Cloud Configuration Management

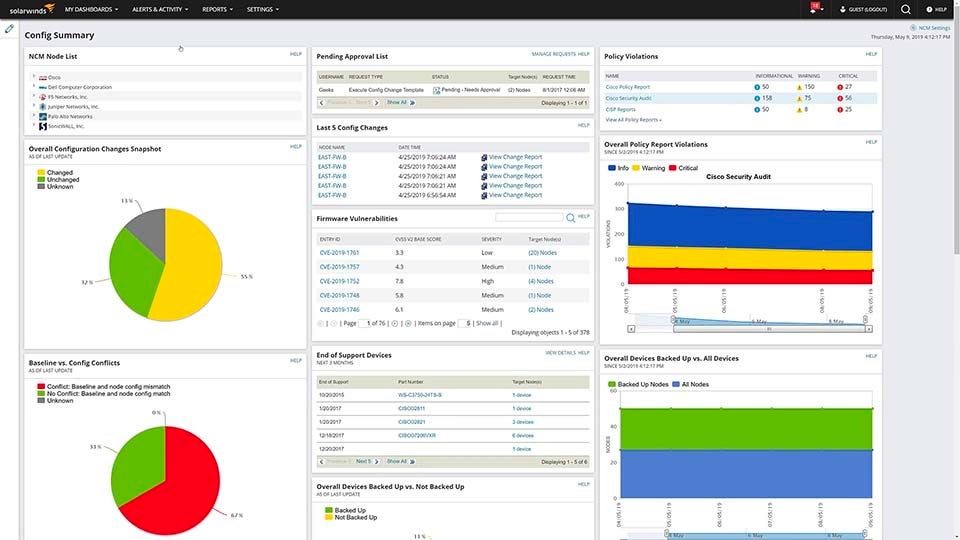
SolarWinds
SolarWinds Network Configuration Manager extends its capabilities to cloud configuration management, offering a solution with features including automatic backups, change tracking, and compliance reporting for cloud-based network infrastructure. Real-time configuration alarms, version control, and bulk modifications are effortlessly applied to cloud setups, assuring stability and compliance. This improves efficiency and performance while managing network setups on-premises and in the cloud.

GitHub
GitHub is a cloud configuration management platform that offers capabilities for smooth collaboration and version control. Its branching and merging capabilities allow teams to work on configuration scripts concurrently, enabling efficient cooperation. The continuous integration (CI) tools automate testing, validation, and deployment procedures, ensuring a consistent and error-free setup. The code review feature improves configuration quality by adhering to best practices and security requirements. The issue tracking and project management features of GitHub further simplify setup processes, providing a holistic solution for cloud infrastructure management teams.

Ansible
Ansible makes IT automation easier by centralizing resource management and allowing for multi-tier deployments. It combines several components, like servers and storage, to ensure known conditions. The agentless design of Ansible decreases configuration time, while modules improve infrastructure automation. Benefits include simplified automation, a low learning curve, and quick deployment in 30 minutes using YAML for simple job descriptions.

Bottom Line: Secure Your Infrastructure with Cloud Configuration Management
With the shifting structure of cloud computing comes the emerging security challenges that demand advanced solutions. Cloud configuration management becomes essential in overcoming these challenges. This process addresses security problems while also reinforcing protection within the dynamic cloud settings by employing a targeted combination of methods, tools, and policies. Elevating the security posture enables enterprises to fully embrace the benefits of cloud computing while properly managing the dangers inherent in evolving technologies.








