As credential attacks become more sophisticated, identity and access management solutions need to become more innovative. Zero trust concepts — assuming no user can be trusted until fully verified — should be applied to both users and devices to help protect sensitive company and customer information.
This guide to zero trust and IAM breaks down these terms, why they’re important, and how they might work together in IT environments. We’ll look at Kolide — this article’s sponsor and a provider of device trust solutions — as one way to increase trust in users accessing applications and IT systems.
What Is Zero Trust IAM (Identity Access Management)?
To understand how zero trust and IAM can work together, it’s best to understand how they work on their own.
- Zero trust is an approach to infrastructure security that never automatically trusts a user before verifying their identity and authorization. Zero trust also doesn’t restrict security to the network perimeter, since plenty of threats can slip through a firewall and move laterally through an organization’s network. Stopping lateral movement and attack escalation is one of the key benefits of zero trust.
- IAM manages both users’ identities and their rights to access company applications and other systems. An IAM tool compares access attempts against stored credentials to determine if a user is who they say they are. It then provides access according to predefined access policies.
Zero trust only permits a user or device once it has proven itself compliant with all of an enterprise’s predefined policies. IAM enforces identity and access management policies. Basically, IAM is a component of zero trust security, but it isn’t everything. The two are not interchangeable, but IAM helps organizations standardize and verify user identities.
Keep in mind that zero trust cannot be achieved by purchasing a single product, and it takes time to implement a comprehensive architecture. However, some vendors offer pieces of the zero trust puzzle, helping employees achieve compliance with their organization’s security goals.
Read more about the challenges of zero trust.
How Can You Add Zero Trust to IAM?
To implement zero trust concepts within your company’s identity and access management, your IT and security teams must rethink each sector of your IT infrastructure. Examples include network access controls, biometrics, and device security.
While no single vendor can give your business an all-encompassing zero trust solution, there are providers who offer specific products to address facets of zero trust. Kolide is one such provider. It’s a security tool that integrates with Okta and focuses on the device part of zero trust. Just because a business decides to trust a device doesn’t mean it’s trustworthy. Kolide authenticates devices as they log into Okta. If a given device doesn’t meet a certain set of activated policies, the device is blocked.
Typically, a zero trust architecture gives IT teams hiccups because every blocked device or user, every set of failed credentials that possibly indicates a breach, must then be routed through them. This often looks like a deluge of support tickets that IT admins must manually sort through. Kolide decreases the manual load on IT teams by providing self-service options for users when a device is blocked.
A security or IT team member has already set a policy to block any devices with insecure browsers. When a user tries to log into Okta and pass the Kolide verification, they’re blocked because their Google Chrome is out of date.
Kolide is designed to help user devices become compliant and to reduce the manual burden on IT teams. Therefore, users aren’t just hung out to dry when their device is blocked. Instead, they have the immediate option to fix the issue. Kolide provides a list of remediation instructions, which users can access simply by clicking the “Details” button (screenshot below).
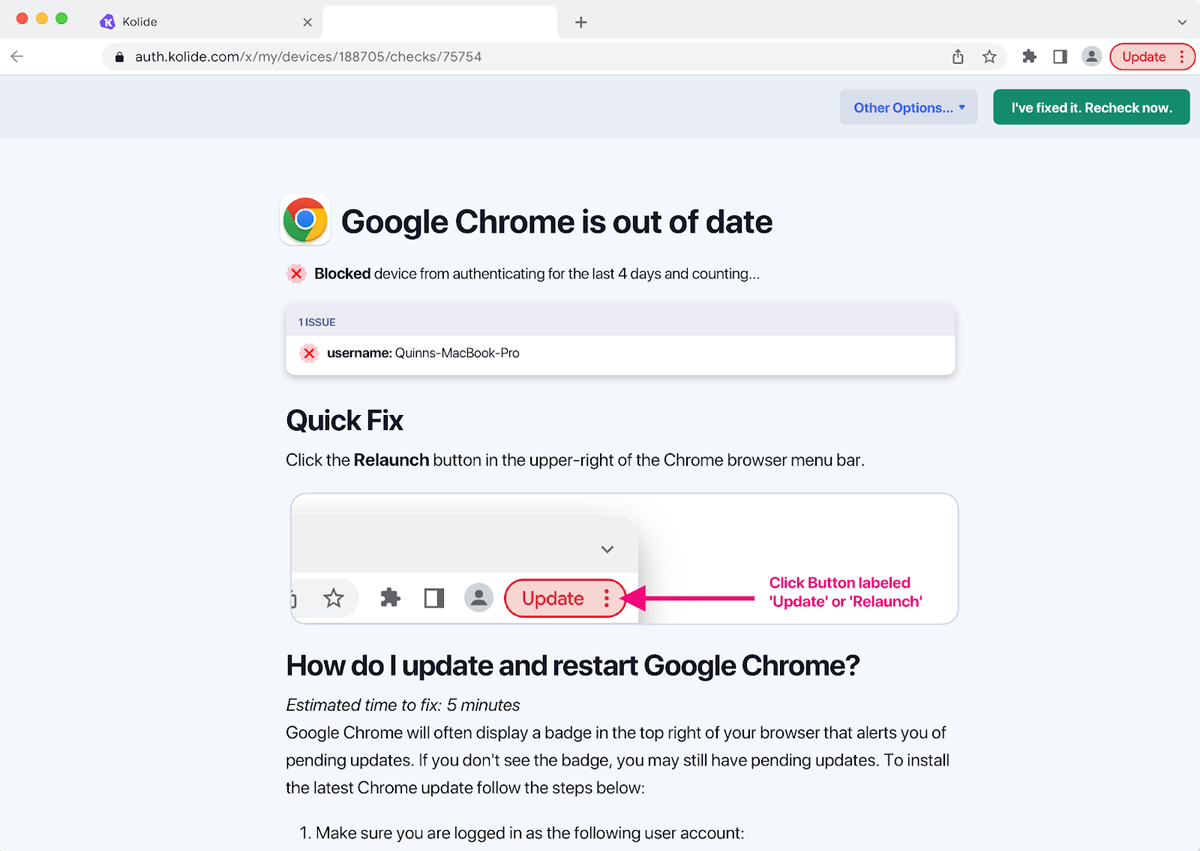
Rather than immediately blocking devices without providing further information, Kolide is intended to show users how to make their devices compliant. If the device is the problem and the issue isn’t identified and fixed, users will continue running into roadblocks when they attempt to access necessary applications. But with software that educates users and tells them why a device has been blocked, employees are able to more quickly solve expired licenses or software updates. And by self-servicing the problem, users reduce the load on IT teams.
By focusing on device vulnerabilities, Kolide can identify issues like Mac computers with bad batteries and Microsoft product installations with falsified or expired licenses. Some of these might just be an update that fell through the cracks, but some could be an unauthorized user from outside the organization.
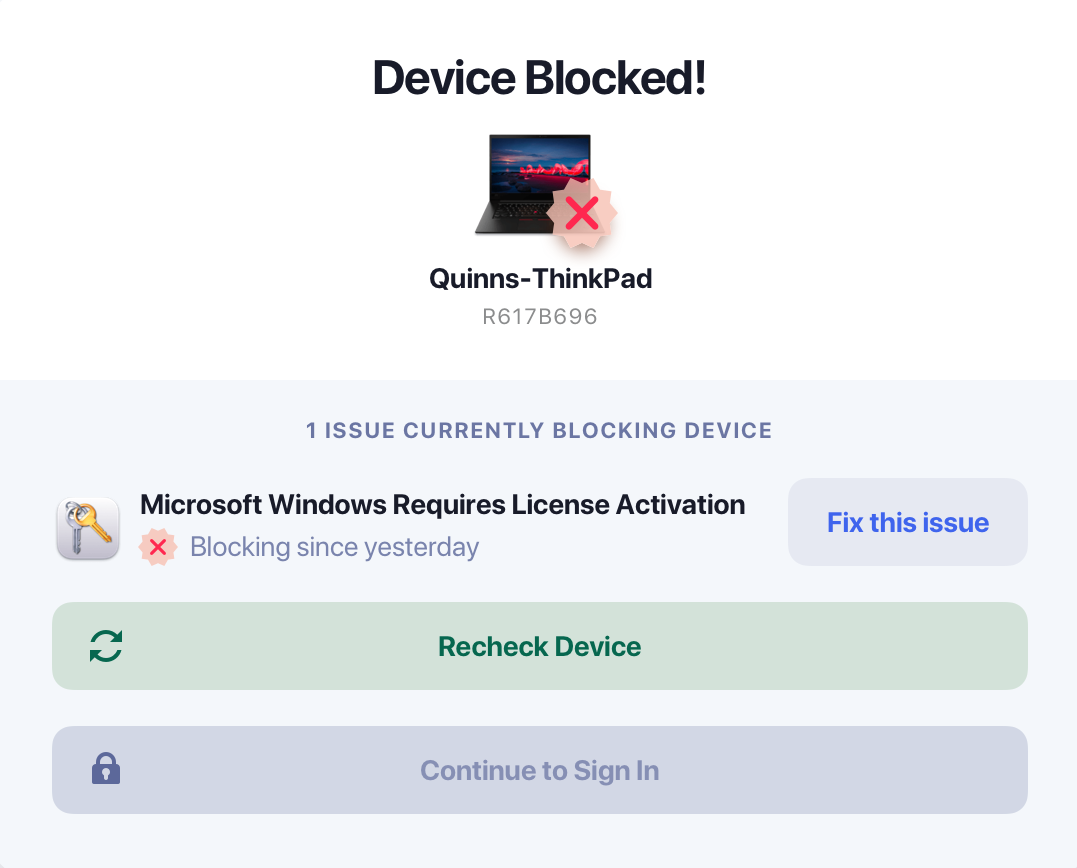
Kolide specifically focuses on the devices attempting to access business services. While a user’s identity might be verifiable, their device’s security could have vulnerabilities or might already be compromised. Kolide doesn’t automatically trust devices until they demonstrate compliance with its policies, which users can configure in accordance with their business’s security strategy.
Going Beyond Identity Management
Although IAM plays a critical role in security infrastructure, its drawback is limited focus, according to Nick Fitzsimmons, VP of Marketing at Kolide. IAM mainly just verifies the user’s identity.
“But that’s only half the battle,” Fitzsimmons said. “A legitimate user can still do a lot of damage if their device is infected with malware. What makes Kolide different from those tools, and other endpoint security tools, is that we can check virtually anything about a device’s posture, and restrict access based on that.”
Additionally, all users must have Kolide on their phone or laptop to authenticate their connection. Threat actors aren’t able to use stolen credentials to log into applications using Kolide.
Compliance-based device authorization is just one example of developing zero trust strategies within a business IT system. Integrating “never trust, always verify” policies within your identity and access management solution — in this case, Okta — helps teams avoid issues that standard IAM might not be able to solve.
Zero trust applies to every sector of your IT infrastructure. It’s not a set-and-forget solution, but it gives businesses a clearer view of their user and device access attempts and the vulnerabilities that plague them.
Learn more about implementing a zero trust infrastructure.
Zero Trust Builds a Granular Security Infrastructure
In cybersecurity, granularity simply means detail and specificity. In other words, can our organization build such specific policies, unique to our needs and security requirements, that we successfully protect our applications and data?
Zero trust builds additional context for identity and access management. For example, Kolide’s approach to policy customization lets teams create very specific rules. Kolide then has context for users’ devices, can determine whether that device complies with predetermined policies, and can block a device if it seems to pose a threat. This is all based on the access criteria that’s important to an individual organization. Zero trust should be customizable.
According to Fitzsimmons, there are two major challenges for businesses to develop zero trust within an existing IAM framework. “The first is that they need to provide real-time device posture at the point of authentication that can align with industry standards and internal policies,” Fitzsimmons said. “This has to be cross-platform and able to go deeper than the basics like hard drive encryption and firewall status.
“The second is that they can’t simply leave users blocked without the context and agency to unblock themselves. This creates the IT bottleneck that often leads to failed Zero Trust implementations.”
It’s critical for users to take on some responsibility for the role they play in zero trust, not least because that helps IT teams focus on their roles within the organization.
Is a granular security infrastructure difficult to implement? It can be. IT and security teams aren’t always used to this level of detail. And zero trust is a relatively new approach to cybersecurity. But it’s worthwhile, especially for enterprises that want to take their protective measures into their own hands.
Bottom Line: Zero Trust and IAM for Enterprises
Keep in mind that device compliance is only one aspect of zero trust. To compile a full zero trust architecture, your organization will have to strategically choose solutions that address zero trust and IAM, integrate well with each other, and make sense for your security requirements. A financial services firm will have different security policies than a locally based nonprofit. However, they can both benefit from a zero trust approach to identity management — it just might look different.
Don’t be discouraged if it takes your IT and security teams a significant amount of time to deploy zero trust concepts, even if you already use an IAM solution. IAM is just one component of zero trust, but it’s a good start. Tools like Kolide can help businesses develop a comprehensive security infrastructure, but don’t be afraid when that process takes time. It’s still one of the best choices you can make for your business’s overall cyber protection.







