While this week was a little light on vulnerability news, it’s still been significant, with Microsoft’s Patch Tuesday happening as well as updates for major products, like Zoom. Akira ransomware vulnerabilities have also surfaced in older Cisco products, and SolarWinds patched some remote code execution flaws in its Access Rights Manager product.
Your IT teams should regularly check your vendors’ security bulletins for any vulnerability news or updates. Also keep an eye on the last few weeks’ vulnerability recaps, especially because we’ve seen repeat products that continue to be exploited.
February 13, 2024
Zoom Fixes Critical Vulnerability in Windows Products
Type of vulnerability: Improper input validation.
The problem: Zoom recently patched a flaw that affected three of its Windows-facing software products: Zoom Desktop Client for Windows, Zoom VDI Client for Windows, and Zoom Meeting SDK for Windows. The vulnerability, an improper input validation flaw, could permit unauthenticated users to access a network and then escalate their privileges.
The vulnerability CVE is CVE-2024-24691. It’s rated as critical, with a score of 9.6.
Zoom’s security bulletin listed the following affected products:
- Zoom Desktop Client for Windows before version 5.16.5
- Zoom VDI Client for Windows before version 5.16.10 (excluding 5.14.14 and 5.15.12)
- Zoom Rooms Client for Windows before version 5.17.0
- Zoom Meeting SDK for Windows before version 5.16.5
The fix: The most recent version of the Zoom client fixes this vulnerability. Users can download it manually by navigating to Zoom’s download page, or automatically by opting to download the latest version when Zoom prompts them to do so.
Microsoft Patch Tuesday Fixes 73 Vulnerabilities
Type of vulnerability: Multiple vulnerabilities, including remote code execution and privilege escalation.
The problem: Microsoft patched 73 vulnerabilities in its most recent Patch Tuesday event, which occurs every month. Among the vulnerabilities is CVE-2024-21412, an Internet Shortcut Files flaw that allows an unauthenticated attacker to send a malicious file to a user. It bypasses Internet Shortcut Files’ security measures.
The fix: Review Microsoft’s list of released updates and associated CVEs to determine which products need to be patched. For CVE-2024-21412 specifically, a user has to click the link for the attack to occur. Ensure that team members don’t open links without verifying directly with the sender.
Does your business need a quick, reliable way to find vulnerabilities? Read our picks for the best vulnerability scanning tools for quality products and key features to consider.
February 15, 2024
Akira Ransomware Affects Old Vulnerability in Cisco Products
Type of vulnerability: Remote unauthenticated access and potential credential data theft.
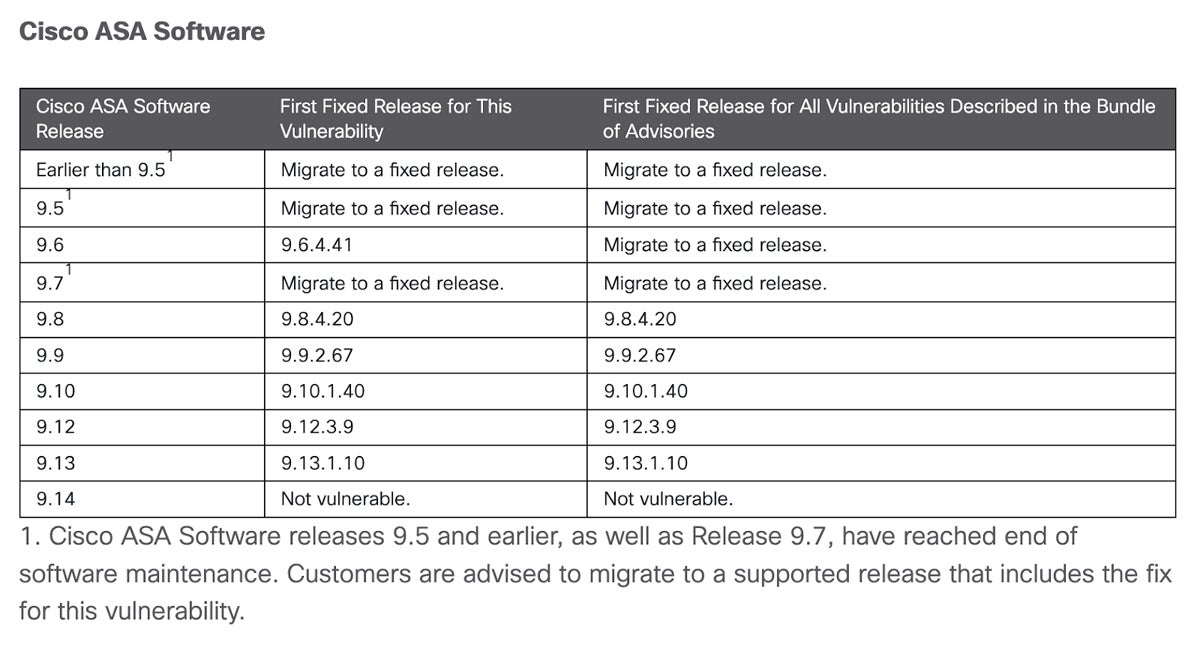
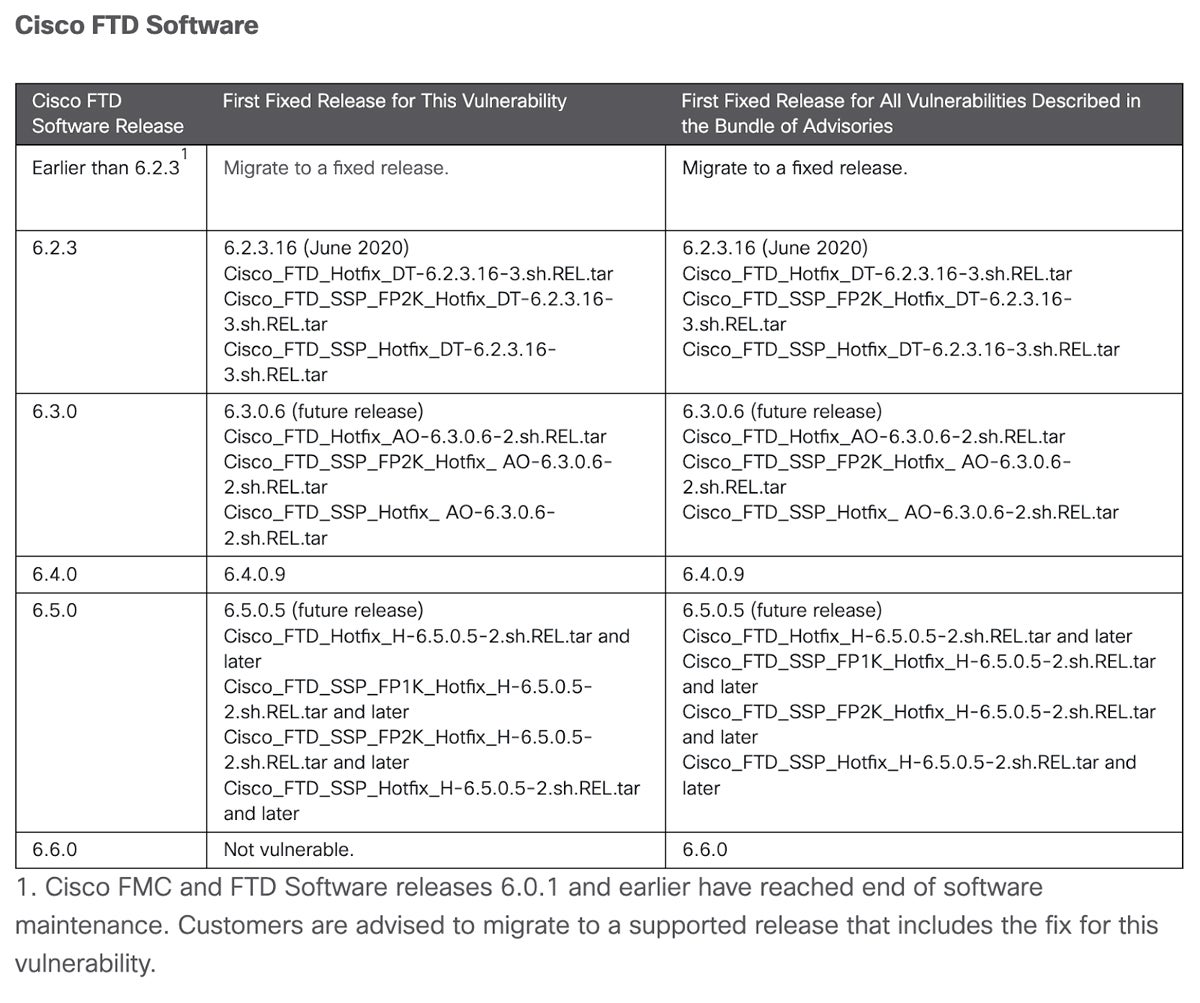
The problem: Researchers at cybersecurity company Truesec uncovered data that indicated Akira ransomware might be exploiting an old vulnerability within Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD). Appliances with affected software must have Anyconnect SSL VPN enabled on whichever interface is exposed to the internet for an attack to occur.
The vulnerability, CVE-2020-3259, was first discovered in May 2020. It allows remote unauthenticated threat actors to steal data from a device’s memory, including credential data. On Thursday, February 15, the Cybersecurity and Infrastructure Security Agency added the vulnerability to its catalog after reports that it might be actively exploited again.
Akira is a particularly dangerous brand of ransomware. Palo Alto’s Unit 42 research team said that Akira led the number of ransomware posts from new leak sites in 2023. Akira also has potential ties to Conti, another ransomware group, through cryptocurrency transactions, according to Unit 42.
The fix: Cisco provides upgrade recommendations for the following affected versions:
Truesec recommends:
- Implementing MFA wherever possible, especially on client VPN connections
- Changing passwords, secrets, and preshared keys
- Enabling logging
- Patching the software to a nonvulnerable version
February 16, 2024
SolarWinds Patches 5 RCE Vulnerabilities in Access Rights Manager
Type of vulnerability: Remote code execution.
The problem: SolarWinds recently patched five remote code execution vulnerabilities in its Access Rights Manager product, which provisions, deprovisions, and manages employee access rights. Three of the vulnerabilities have a critical CVE rating. The vulnerabilities affect version v2023.2 of Access Rights Manager. SolarWinds recently fixed the vulnerabilities.
Amongst the flaws were deserialization of untrusted data RCE, directory traversal RCE, and traversal RCE. The CVEs are CVE-2023-40057, CVE-2024-23476, CVE-2024-23477, CVE-2024-23478, and CVE-2024-23479.
The fix: Upgrade all older versions of Access Rights Manager to 2023.2.3, which fixes all five of the RCE vulnerabilities.
February 19, 2024
ExpressVPN Split Tunneling Disabled after Discovered Vulnerability
Type of vulnerability: DNS traffic leak.
The problem: A VPN expert recently gave Express VPN a tip about its split tunneling feature, which allows some traffic to pass through the VPN and blocks other traffic. The DNS traffic wasn’t traveling to the ExpressVPN servers like it was supposed to, but instead to a third-party server. The vulnerability exists in ExpressVPN Version 12 for Windows. ExpressVPN temporarily disabled split tunneling on that platform.
The split tunneling feature will remain inactive until ExpressVPN engineers have time to research and mitigate the issue, according to the vendor. ExpressVPN first published the bulletin about this vulnerability early in February but updated it in the middle of the month.
If teams need to use the split tunneling feature, they can use Version 10 of ExpressVPN, which doesn’t have the same flaw.
The fix: ExpressVPN disabled split tunneling in Version 12, so it’ll no longer be an issue for that product.
Read next:
- VulnRecap 2/12/24 — Ivanti, JetBrains, Fortinet, Linux Issues
- 6 Best Vulnerability Management Software & Systems in 2024










