How to Perform a Content Migration - Your Checklist for Success
AIIM
DECEMBER 19, 2019
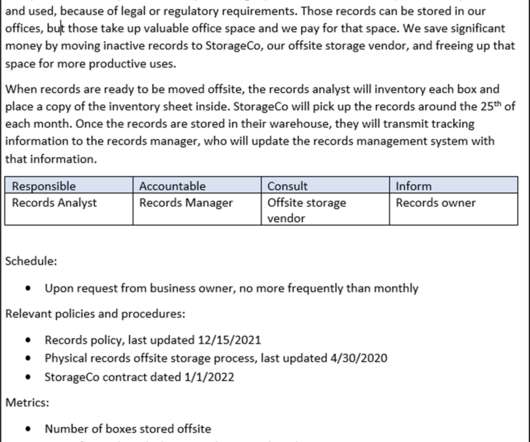
In this blog post, we present an approach and checklist for migrating your information from one system to another. While the details will differ depending on a number of factors (the systems being migrated from and to, the nature of the information being migrated, etc.), Content Migration Phase 1: Strategy. Preparation.



















Let's personalize your content