
Researchers say mobile malware purveyors have been abusing a bug in the Google Android platform that lets them sneak malicious code into mobile apps and evade security scanning tools. Google says it has updated its app malware detection mechanisms in response to the new research.
At issue is a mobile malware obfuscation method identified by researchers at ThreatFabric, a security firm based in Amsterdam. Aleksandr Eremin, a senior malware analyst at the company, told KrebsOnSecurity they recently encountered a number of mobile banking trojans abusing a bug present in all Android OS versions that involves corrupting components of an app so that its new evil bits will be ignored as invalid by popular mobile security scanning tools, while the app as a whole gets accepted as valid by Android OS and successfully installed.
“There is malware that is patching the .apk file [the app installation file], so that the platform is still treating it as valid and runs all the malicious actions it’s designed to do, while at the same time a lot of tools designed to unpack and decompile these apps fail to process the code,” Eremin explained.
Eremin said ThreatFabric has seen this malware obfuscation method used a few times in the past, but in April 2023 it started finding many more variants of known mobile malware families leveraging it for stealth. The company has since attributed this increase to a semi-automated malware-as-a-service offering in the cybercrime underground that will obfuscate or “crypt” malicious mobile apps for a fee.
Eremin said Google flagged their initial May 9, 2023 report as “high” severity. More recently, Google awarded them a $5,000 bug bounty, even though it did not technically classify their finding as a security vulnerability.
“This was a unique situation in which the reported issue was not classified as a vulnerability and did not impact the Android Open Source Project (AOSP), but did result in an update to our malware detection mechanisms for apps that might try to abuse this issue,” Google said in a written statement.
Google also acknowledged that some of the tools it makes available to developers — including APK Analyzer — currently fail to parse such malicious applications and treat them as invalid, while still allowing them to be installed on user devices.
“We are investigating possible fixes for developer tools and plan to update our documentation accordingly,” Google’s statement continued.
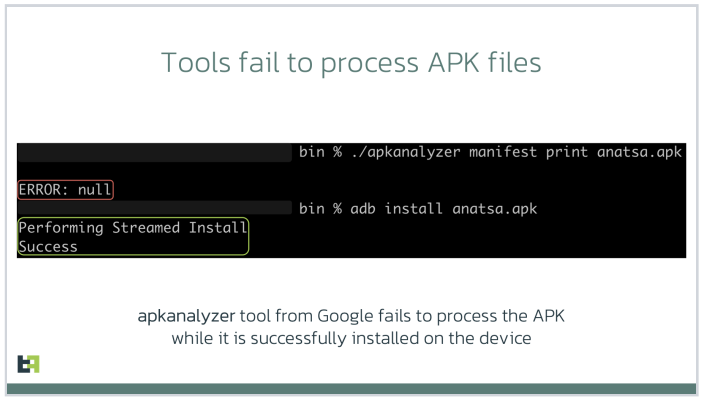
Image: ThreatFabric.
According to ThreatFabric, there are a few telltale signs that app analyzers can look for that may indicate a malicious app is abusing the weakness to masquerade as benign. For starters, they found that apps modified in this way have Android Manifest files that contain newer timestamps than the rest of the files in the software package.
More critically, the Manifest file itself will be changed so that the number of “strings” — plain text in the code, such as comments — specified as present in the app does match the actual number of strings in the software.
One of the mobile malware families known to be abusing this obfuscation method has been dubbed Anatsa, which is a sophisticated Android-based banking trojan that typically is disguised as a harmless application for managing files. Last month, ThreatFabric detailed how the crooks behind Anatsa will purchase older, abandoned file managing apps, or create their own and let the apps build up a considerable user base before updating them with malicious components.
ThreatFabric says Anatsa poses as PDF viewers and other file managing applications because these types of apps already have advanced permissions to remove or modify other files on the host device. The company estimates the people behind Anatsa have delivered more than 30,000 installations of their banking trojan via ongoing Google Play Store malware campaigns.
Google has come under fire in recent months for failing to more proactively police its Play Store for malicious apps, or for once-legitimate applications that later go rogue. This May 2023 story from Ars Technica about a formerly benign screen recording app that turned malicious after garnering 50,000 users notes that Google doesn’t comment when malware is discovered on its platform, beyond thanking the outside researchers who found it and saying the company removes malware as soon as it learns of it.
“The company has never explained what causes its own researchers and automated scanning process to miss malicious apps discovered by outsiders,” Ars’ Dan Goodin wrote. “Google has also been reluctant to actively notify Play users once it learns they were infected by apps promoted and made available by its own service.”
The Ars story mentions one potentially positive change by Google of late: A preventive measure available in Android versions 11 and higher that implements “app hibernation,” which puts apps that have been dormant into a hibernation state that removes their previously granted runtime permissions.




Are there any recommendations for current Android users?
Was this bug patched in the July security update?
I just checked my Android and was still on the June 2023 security update and July 2023 was available.
Buy an iPhone.
The iOS platform has been affected by plenty of vulnerabilities. The only thing I know is an advantage over Android is Apple supports their devices for a longer amount of time.
Details…
True but not entirely accurate. Apple will support their devices for (at least) 5 years after it stops selling them. With the Android environment you are at the whim of the device maker as far as updates go. Take your pick of Android phone makers and they all have stunk as far as maintaining devices for more than 2 to 3 years after release. That might have changed a bit in the last few years but I am still not aware of any of them doing what Apple does for security / maintenance of the OS on their devices.
If you are a corporation who is rolling out devices to the masses, and are both fiscal and security conscience, unless you are buying throw away Android devices, I fail to see how any Android device would be the answer from either perspective. Apple is not without its flaws but at least you know they will release (somewhat) timely updates. LG, Samsung, etc….good luck because they all think they need to add their own “flavor” to the OS.
iOS is subject to vulnerabilities too…
I will give Apple props for supporting their devices for much longer than any other phone manufacturer.
Try to avoid direct whattaboutism, it’s not a great look for “security” (or theater)…
bleepingcomputer.com/news/security/google-android-patch-gap-makes-n-days-as-dangerous-as-zero-days/
bitdefender.com/blog/hotforsecurity/n-day-vulnerabilities-pose-major-threat-to-android-users-google-report-shows/
(or any source you prefer)
“An example of this issue is the ARM Mali GPU bug. This Android flaw was reported in July 2022. The Android Security Team referred the issue to ARM instead, labeling it a “Won’t Fix” situation due to its device-specific nature. ARM then released a new, patched driver version in October 2022. However, it wasn’t until November 2022 that Google’s Threat Analysis Group (TAG) found the bug being exploited in the wild. Even though ARM had already released a patch, the complete fix for the vulnerability was rolled out on Android in April 2023. This was six months after ARM’s patch release, nine months after the initial reporting, and five months after it was found being exploited in the wild.”
That’s ON TOP OF Android’s version segmentation issues. Think about what that means.
Thanks for the report! How can Android owners check their devices to see if they’re affected?
Goog play store has been the most prolific spreader of malware by volume than any other single source for so many years.
Although they Require an Email to download apps, they never send notices to people that an app they downloaded from goog was malicious, nor provide advice on remediation. I am very surprised there hasn’t been a class action suit filed against them for negligence.
Bluntly it’s the main reason to avoid android, (second is their own spying).
Well lets be honest with any of the official tools for viewing a compiled application. They fall over with any amount of basic tricks for resources/sources. They don’t have any of the same robust handling like jadx, jeb, apktool, apkid, etc have.
Love the images you use to represent the article. I’m still laughing at that little digital guy with the wrench.
Eye-opening article! It’s crucial for us to stay vigilant about the apps we download and grant permissions to on our Android devices. The insights shared here shed light on the cunning tactics malicious apps use to infiltrate our devices. Let’s all prioritize security and ensure we only download apps from trusted sources.
To make sure my device is not infected by malicious apps I only use really popular apps.
http://www.bleepingcomputer.com/news/security/trojanized-signal-and-telegram-apps-on-google-play-delivered-spyware/
Signal and Telegram, pretty popular.
Watering holes are full of beasts.
I’m constantly searching on the internet for posts that will help me. Too much is clearly to learn about this. I believe you created good quality items in Functions also. Keep working, congrats!
Is there a typo in this line:
More critically, the Manifest file itself will be changed so that the number of “strings” — plain text in the code, such as comments — specified as present in the app does match the actual number of strings in the software.
Should it be “doesn’t match” ? Thanks.
Also which specific “manifest” file is being referred to here ? Typical manifest file in Android apps doesn’t store number of strings in the app.