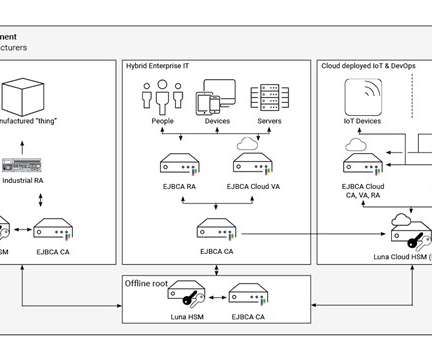
Webinar: The Supply Chain Security Gap: Impacts on Connected and Embedded Device Manufacturers via Embedded Computing Design on February 9th, 2022 at 2pm Eastern
IG Guru
FEBRUARY 2, 2022
The post Webinar: The Supply Chain Security Gap: Impacts on Connected and Embedded Device Manufacturers via Embedded Computing Design on February 9th, 2022 at 2pm Eastern appeared first on IG GURU. Ponemon was appointed to the Advisory Committee for Online…Full Profile Rich Nass Executive Vice-President, Brand […].









































Let's personalize your content