Mozi infections will slightly decrease but it will stay alive for some time to come
Security Affairs
SEPTEMBER 1, 2021
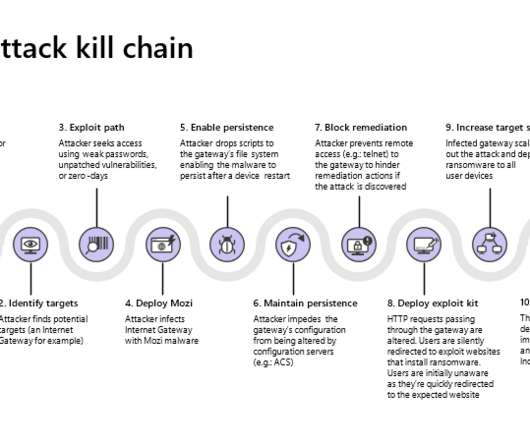
The Mozi botnet was spotted by security experts from 360 Netlab, at the time of its discovered it was actively targeting Netgear, D-Link, and Huawei routers by probing for weak Telnet passwords to compromise them. “The discovery of Mozi_ftp, Mozi_ssh gives us clear evidence that the Mozi botnet is also trying to profit from mining.

























Let's personalize your content