Ransomware Hackers May Be Exploiting Aiohttp Library Bug
Data Breach Today
MARCH 18, 2024
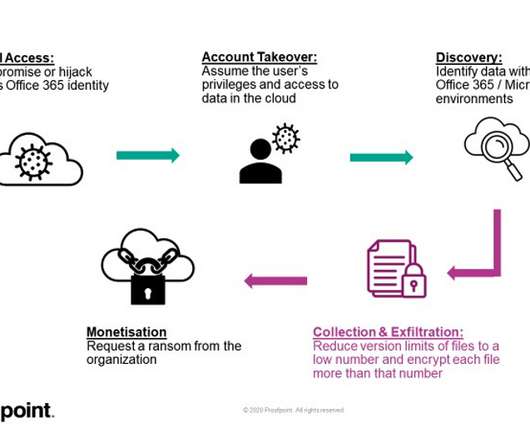
The Python Library Flaw Allows Directory Traversal Attacks Hackers who are possibly members of a criminal group affiliated with numerous ransomware-as-a-service operations are exploiting a directory traversal vulnerability in a Python library that allows unauthenticated remote attackers access to sensitive information from server files.


































Let's personalize your content