Hackers have found a way to infect Windows Event Logs with fileless malware, security researchers have found.
Kaspersky researchers on May 4 revealed “a new stash for fileless malware.” During a “very targeted” campaign, hackers used Windows Event Logs to inject shellcode payloads and operate stealthily.
This new approach is highly sophisticated yet could still become popular, as it seems quite efficient for injecting malicious DLL and evading detection. Kaspersky researchers discovered that the attackers used various tools, including custom and commercial solutions like Cobalt Strike and a new toolset used by the hackers.
The researchers said it’s clearly the work of an advanced threat actor but they could not attribute the campaign to a known APT group. The campaign is dubbed “SilentBreak” for now, after the name of the toolset used by the hackers.
Also read: How Cobalt Strike Became a Favorite Tool of Hackers
SilentBreak’s Attack Techniques
The researchers were struck by “the variety of the campaign’s techniques and modules,” so they made a classification to analyze the modules one by one:
All these stages were possible because the hackers managed to trick a target into downloading an infected .rar on file.io, a legitimate website. After that, they were able to spread a digitally-signed Cobalt Strike module to exfiltrate sensitive data.
How the Attackers Injected Code in Windows Logs
The researchers discovered malicious payloads into Windows event logs for the Key Management Services (KMS):
To achieve the first stage in their campaign, the hackers used a custom malware dropper that copies the legitimate Windows Error Reporting executable (WerFault.exe) to C:\Windows\Tasks, and then drops a malicious binary in the same directory:
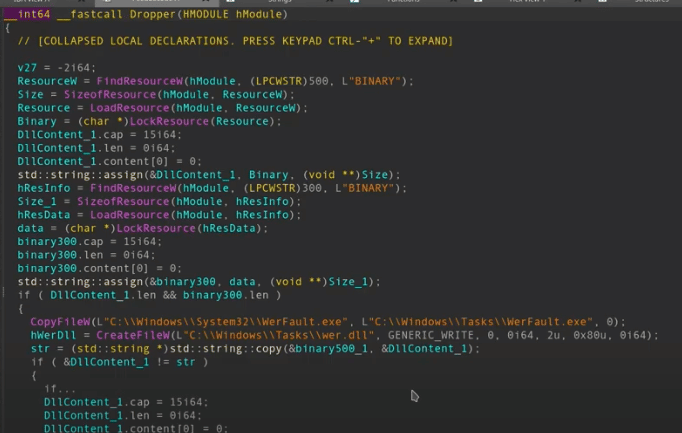
This technique is called DLL hijacking and consists of replacing a required DLL file with a malicious one and placing it in the same directory as the targeted application. The system uses DLL (Dynamic Link Library) files to store some resources the application needs and will load automatically.
The new WerFault.exe is then set to autorun, which creates a “Windows Problem Reporting value in the Software\Microsoft\Windows\CurrentVersion\Run Windows system registry branch.”
The dropper then looks for logs with a specific category (0x4142) and with the KMS as a source. If it does not find one, the encrypted shell code is written in 8KB chunks in the event logs.
Kaspersky researchers explored the code and discovered it acts as a proxy to intercept all calls to the original library (the legitimate one) and prepare the next stages, which indicates an iterative procedure.
Hackers Focused on Evasion
The top priority for this operation was obviously to remain undetected. To achieve that, the attackers used various anti-detection techniques such as:
- a legitimate digital certificate to sign malicious files
- autorunned copies of legitimate executable (Werfault.exe)
- anti-detection wrappers compiled in various languages such as Go or C++
- obfuscated function names in code
- malicious instructions split into chunks of shell code in the Windows Event Logs
The malware analysis by Kaspersky is quite remarkable and detailed. The researchers had to write custom scripts to decrypt all the hidden areas.
According to the researches, the most unusual and innovative aspect of the SilentBreak campaign is the “Encrypted shellcode divided into 8 KB blocks and saved in the binary part of event log.”
During the second stage, the hackers used custom decryptor launchers for Cobalt Strike to decrypt the shell code and map it into memory and ultimately execute the malicious instructions and deploy malware.
Also read: How Hackers Evade Detection
The Campaign Relied on Trojans
The attackers used two types of Trojans:
- HTTP-based Trojan with C2 (command and control)
- Named-pipe based Trojan
The encrypted shell code in event logs contained very specific arguments such as the address of next stage Trojan or the hashes of function names used inside the Trojan.
There were also unused strings like “dave” and the constant “4.” The researchers believed the launcher might support other modules that require additional parameters, which could explain such artifacts.
The HTTP Trojan seems to generate fingerprinting-containing information such as the computer name, the local IP addresses, the OS version, the architecture (x86 or x64), and the values of MachineGUID.
This information is then used to send targeted instructions through the rogue communication channel (C2).
According to the researchers, the named-pipe Trojan has “a more profound command system,” including privilege escalation, taking screenshots, or measuring inactivity time.
How to Protect Against Event Log Attacks
Such a high degree of preparation and the time spent on writing custom modules and decryptors suggest the work of an advanced hacking group that remains unidentified at the time of writing.
There’s not much you can do to anticipate such high-profile attacks, and antivirus software or built-in firewalls aren’t likely to catch them. However, you can take concrete measures like using EDR and other endpoint security solutions to increase your chances of detecting unusual and suspicious activities, particularly if those solutions have a behavioral component.
A zero trust architecture may also help to contain the infection, as here, for example, the hackers had a strategy to spread their malware and iterate the infection cycle.
Security vendors and knowledge bases such as MITRE ATT&CK are likely to add this new approach to their catalogs in coming months. In any case, that would be a good idea to help security teams map the technique for threat intelligence purposes.
Read next:






