Fake Smart Factory Honeypot Highlights New Attack Threats
Threatpost
JANUARY 24, 2020
The honeypot demonstrates the various security concerns plaguing vulnerable industrial control systems.

Threatpost
JANUARY 24, 2020
The honeypot demonstrates the various security concerns plaguing vulnerable industrial control systems.
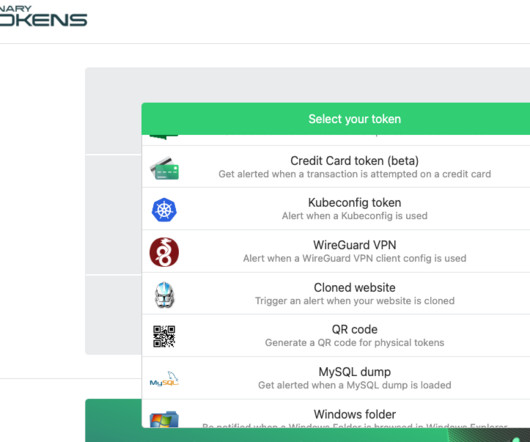
Krebs on Security
AUGUST 22, 2023
. “Canarytokens does all this and more, letting you implant traps in your production systems rather than setting up separate honeypots.” But in an interview with KrebsOnSecurity, Thinkst founder and CEO Haroon Meer said most deception techniques involve some degree of hubris. “Nobody really has time for that.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dark Reading
DECEMBER 19, 2018
While you prepare your defenses against the next big thing, also pay attention to the longstanding threats that the industry still hasn't put to rest.

Dark Reading
JANUARY 21, 2020
A fictitious industrial company with phony employees personas, website, and PLCs sitting on a simulated factory network fooled malicious hackers - and raised alarms for at least one white-hat researcher who stumbled upon it.

Security Affairs
FEBRUARY 18, 2019
Cybersecurity expert Marco Ramilli shared another tool of his arsenal that extracts suspicious IPs from undesired connections, his HoneyPots. In other words: HoneyPots. I run a personal HoneyPot network which stands from years and over time it harvested numerous IP addresses which could be, potentially, malicious (typically scanners).

The Security Ledger
JANUARY 23, 2024
Software is now central to the operation of our economy – as digital transformation washes over every industry. Niels Provos has a storied, two decade career on the forefront of cybersecurity, starting in the late 1990s with his work as a graduate student on phenomena like steganography and honeypots.

Dark Reading
JANUARY 16, 2018
Free online sandbox, honeypot tool simulates a real-world industrial network environment.
Let's personalize your content