PurpleFox malware infected at least 2,000 computers in Ukraine
Security Affairs
FEBRUARY 2, 2024
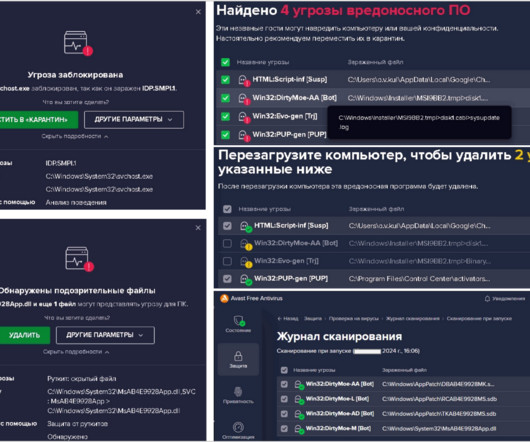
The Windows botnet has been active since late 2017, it was mainly used to mine cryptocurrency, but it was also involved in DDoS attacks in 2018. The malware uses exploits for known vulnerabilities and password brute-forcing attacks for self-propagation. ” reads the alert published by CERT-UA.















































Let's personalize your content