Getting Started with Microsoft 365 Governance
AIIM
NOVEMBER 22, 2022
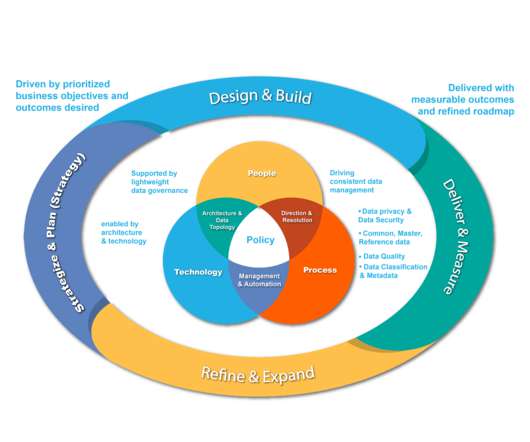
There are no video meetings, digital whiteboards, or real-time document collaboration tools. Good governance ensures that security and management requirements can be met without sacrificing productivity. Ten Tips for Applying Information Governance to Microsoft 365. So it's vital that you have a governance structure for them.















































Let's personalize your content