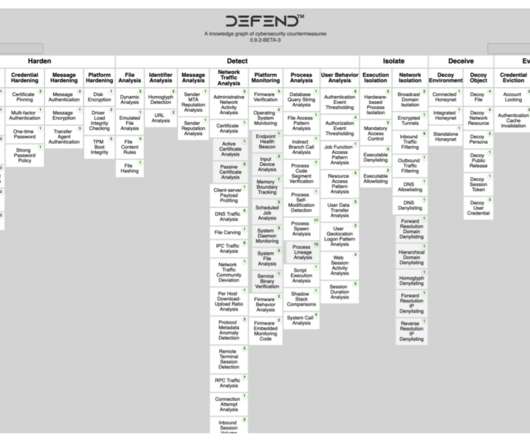
GAO: After Equifax Breach, KBA No Longer Effective
Data Breach Today
JUNE 17, 2019
New Report Calls for Other Methods of Authentication at Federal Agencies Some federal agencies inappropriately continue to rely on knowledge-based authentication to prevent fraud and abuse even though this method is no longer trustworthy because so much personal information that's been breached is readily available to fraudsters, a new U.S.














































Let's personalize your content