U.S. Secret Service: “Massive Fraud” Against State Unemployment Insurance Programs
Krebs on Security
MAY 16, 2020
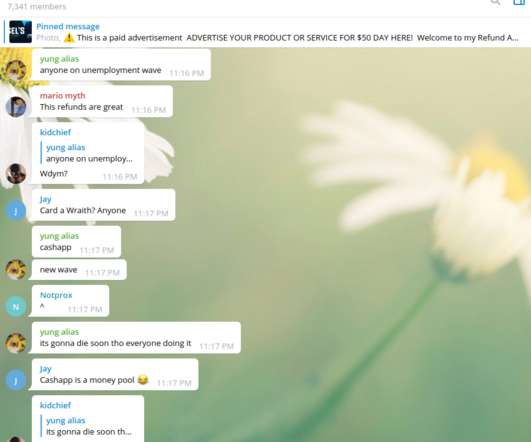
A well-organized Nigerian crime ring is exploiting the COVID-19 crisis by committing large-scale fraud against multiple state unemployment insurance programs, with potential losses in the hundreds of millions of dollars, according to a new alert issued by the U.S. Secret Service. million in phony claims.

















































Let's personalize your content